1.6. グローバルIPアドレス2個を利用した他拠点とのIPsec接続(NAT+下側のみVRRP冗長構成)¶
本構成はVPNトンネルインターフェイス(st)を利用したサイト間IPsec-VPNを構築しています。
トンネルインターフェイス(st)に付与するIPアドレスは、トンネル接続用セグメントとなるため、既存で利用していないセグメントを割り当てください。
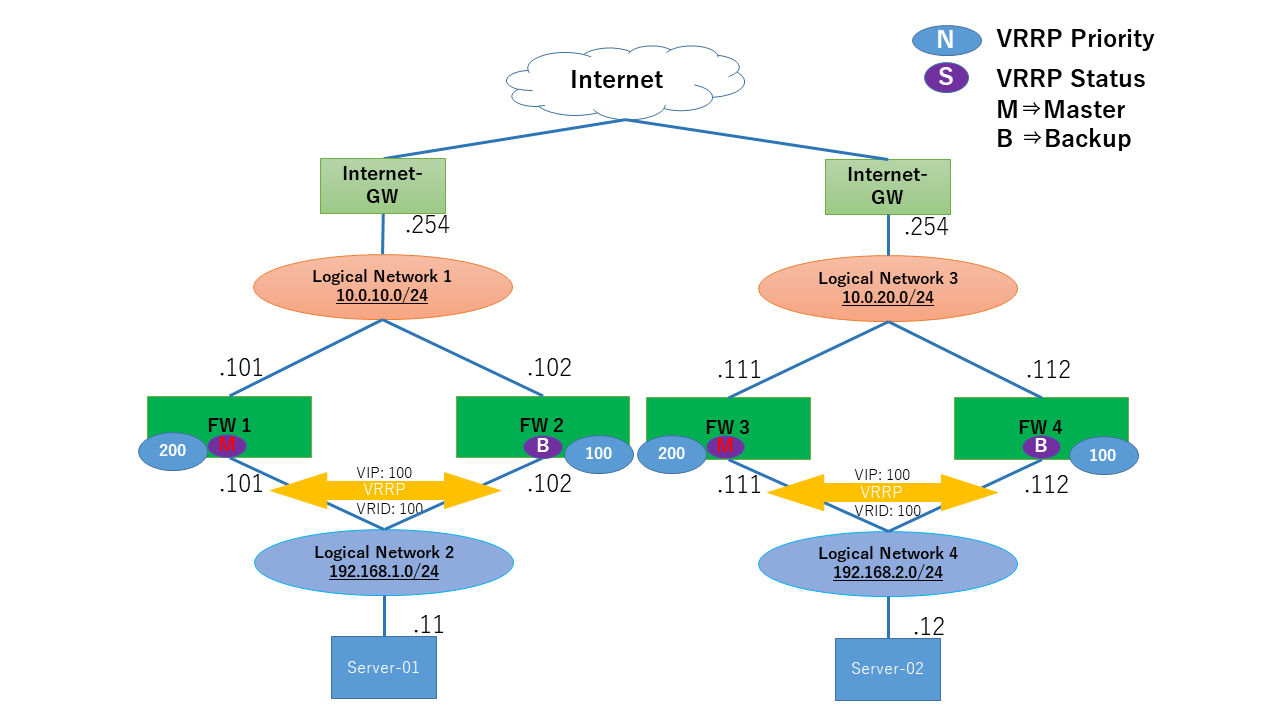
システム構成図のとおり、2つのIPsecトンネルを張り、VRRPでVPNトンネルインターフェイス(st)をトラッキングすることにより冗長構成を実現しています。
IPsecの接続先にVRRPの仮想IPアドレス(以下VIP)を設定することができないため、冗長構成をとる場合は本構成例を推奨します。
本ドキュメントでは各ファイアウォール(以下FW)のグローバルIPアドレスが、FW1は「203.0.113.1/32」、FW2は「203.0.113.2/32」、FW3は「203.0.113.3/32」、FW4は「203.0.113.4/32」として記載します。
1.6.1. システム構成図¶
1.6.2. ファイアウォール設定の内容¶
インターフェイス設定
構成図のとおりIPアドレス設定をします。
FW1
set interfaces ge-0/0/1 unit 0 family inet address 10.0.10.101/24
set interfaces ge-0/0/2 unit 0 family inet address 192.168.1.101/24
set interfaces lo0 unit 0 family inet address 203.0.113.1/32
set interfaces st0 unit 0 family inet address 10.1.1.101/24
FW2
set interfaces ge-0/0/1 unit 0 family inet address 10.0.10.102/24
set interfaces ge-0/0/2 unit 0 family inet address 192.168.1.102/24
set interfaces lo0 unit 0 family inet address 203.0.113.2/32
set interfaces st0 unit 0 family inet address 10.1.2.102/24
FW3
set interfaces ge-0/0/1 unit 0 family inet address 10.0.20.111/24
set interfaces ge-0/0/3 unit 0 family inet address 192.168.2.111/24
set interfaces lo0 unit 0 family inet address 203.0.113.3/32
set interfaces st0 unit 0 family inet address 10.1.1.111/24
FW4
set interfaces ge-0/0/1 unit 0 family inet address 10.0.20.112/24
set interfaces ge-0/0/3 unit 0 family inet address 192.168.2.112/24
set interfaces lo0 unit 0 family inet address 203.0.113.4/32
set interfaces st0 unit 0 family inet address 10.1.2.112/24
インターフェイスのゾーン設定
FW01のゾーン設定
set security zones security-zone trust interfaces ge-0/0/2.0 host-inbound-traffic system-services all
set security zones security-zone trust interfaces ge-0/0/2.0 host-inbound-traffic protocols vrrp
set security zones security-zone untrust interfaces ge-0/0/1.0
set security zones security-zone untrust interfaces lo0.0 host-inbound-traffic system-services ike
set security zones security-zone untrust interfaces st0.0
FW02のゾーン設定
set security zones security-zone trust interfaces ge-0/0/2.0 host-inbound-traffic system-services all
set security zones security-zone trust interfaces ge-0/0/2.0 host-inbound-traffic protocols vrrp
set security zones security-zone untrust interfaces ge-0/0/1.0
set security zones security-zone untrust interfaces lo0.0 host-inbound-traffic system-services ike
set security zones security-zone untrust interfaces st0.0
FW03のゾーン設定
set security zones security-zone trust interfaces ge-0/0/3.0 host-inbound-traffic system-services all
set security zones security-zone trust interfaces ge-0/0/3.0 host-inbound-traffic protocols vrrp
set security zones security-zone untrust interfaces ge-0/0/1.0
set security zones security-zone untrust interfaces lo0.0 host-inbound-traffic system-services ike
set security zones security-zone untrust interfaces st0.0
FW04のゾーン設定
set security zones security-zone trust interfaces ge-0/0/3.0 host-inbound-traffic system-services all
set security zones security-zone trust interfaces ge-0/0/3.0 host-inbound-traffic protocols vrrp
set security zones security-zone untrust interfaces ge-0/0/1.0
set security zones security-zone untrust interfaces lo0.0 host-inbound-traffic system-services ike
set security zones security-zone untrust interfaces st0.0
ゾーンベースファイアウォールのポリシー設定
FW01ならびにFW02のゾーン間のポリシー設定
set security address-book global address LOCAL_LAN 192.168.1.0/24
set security address-book global address REMOTE_LAN 192.168.2.0/24
set security policies from-zone trust to-zone trust policy default-permit match source-address any
set security policies from-zone trust to-zone trust policy default-permit match destination-address any
set security policies from-zone trust to-zone trust policy default-permit match application any
set security policies from-zone trust to-zone trust policy default-permit then permit
set security policies from-zone trust to-zone untrust policy default-permit match source-address any
set security policies from-zone trust to-zone untrust policy default-permit match destination-address any
set security policies from-zone trust to-zone untrust policy default-permit match application any
set security policies from-zone trust to-zone untrust policy default-permit then permit
set security policies from-zone untrust to-zone trust policy fromIPSEC match source-address REMOTE_LAN
set security policies from-zone untrust to-zone trust policy fromIPSEC match destination-address LOCAL_LAN
set security policies from-zone untrust to-zone trust policy fromIPSEC match application any
set security policies from-zone untrust to-zone trust policy fromIPSEC then permit
set security policies from-zone untrust to-zone trust policy DENY-ALL match source-address any
set security policies from-zone untrust to-zone trust policy DENY-ALL match destination-address any
set security policies from-zone untrust to-zone trust policy DENY-ALL match application any
set security policies from-zone untrust to-zone trust policy DENY-ALL then deny
FW03 ならびに FW04 のゾーン間のポリシー設定
set security address-book global address LOCAL_LAN 192.168.2.0/24
set security address-book global address REMOTE_LAN 192.168.1.0/24
set security policies from-zone trust to-zone trust policy default-permit match source-address any
set security policies from-zone trust to-zone trust policy default-permit match destination-address any
set security policies from-zone trust to-zone trust policy default-permit match application any
set security policies from-zone trust to-zone trust policy default-permit then permit
set security policies from-zone trust to-zone untrust policy default-permit match source-address any
set security policies from-zone trust to-zone untrust policy default-permit match destination-address any
set security policies from-zone trust to-zone untrust policy default-permit match application any
set security policies from-zone trust to-zone untrust policy default-permit then permit
set security policies from-zone untrust to-zone trust policy fromIPSEC match source-address REMOTE_LAN
set security policies from-zone untrust to-zone trust policy fromIPSEC match destination-address LOCAL_LAN
set security policies from-zone untrust to-zone trust policy fromIPSEC match application any
set security policies from-zone untrust to-zone trust policy fromIPSEC then permit
set security policies from-zone untrust to-zone trust policy DENY-ALL match source-address any
set security policies from-zone untrust to-zone trust policy DENY-ALL match destination-address any
set security policies from-zone untrust to-zone trust policy DENY-ALL match application any
set security policies from-zone untrust to-zone trust policy DENY-ALL then deny
VRRP設定
VRRP設定前に、必ずSmart Data Platformポータル(以下SDPFポータル)上で、該当インターフェイスにVRRP通信設定の登録をします。 ( VRRP用通信設定の登録 を参考にして、VRRP用通信設定を登録してください。) 正常時にFW01、03がMasterになるように設定をします。
FW01
set security zones security-zone trust interfaces ge-0/0/2.0 host-inbound-traffic protocols vrrp
set interfaces ge-0/0/2 unit 0 family inet address 192.168.1.101/24 vrrp-group 100 virtual-address 192.168.1.100
set interfaces ge-0/0/2 unit 0 family inet address 192.168.1.101/24 vrrp-group 100 priority 200
set interfaces ge-0/0/2 unit 0 family inet address 192.168.1.101/24 vrrp-group 100 preempt
set interfaces ge-0/0/2 unit 0 family inet address 192.168.1.101/24 vrrp-group 100 accept-data
set interfaces ge-0/0/2 unit 0 family inet address 192.168.1.101/24 vrrp-group 100 advertise-interval 5
set interfaces ge-0/0/2 unit 0 family inet address 192.168.1.101/24 vrrp-group 100 track interface st0 priority-cost 200
FW02
set security zones security-zone trust interfaces ge-0/0/2.0 host-inbound-traffic protocols vrrp
set interfaces ge-0/0/2 unit 0 family inet address 192.168.1.102/24 vrrp-group 100 virtual-address 192.168.1.100
set interfaces ge-0/0/2 unit 0 family inet address 192.168.1.102/24 vrrp-group 100 priority 100
set interfaces ge-0/0/2 unit 0 family inet address 192.168.1.102/24 vrrp-group 100 preempt
set interfaces ge-0/0/2 unit 0 family inet address 192.168.1.102/24 vrrp-group 100 accept-data
set interfaces ge-0/0/2 unit 0 family inet address 192.168.1.102/24 vrrp-group 100 advertise-interval 5
FW03
set interfaces ge-0/0/3 unit 0 family inet address 192.168.2.111/24 vrrp-group 210 virtual-address 192.168.2.110
set interfaces ge-0/0/3 unit 0 family inet address 192.168.2.111/24 vrrp-group 210 priority 200
set interfaces ge-0/0/3 unit 0 family inet address 192.168.2.111/24 vrrp-group 210 preempt
set interfaces ge-0/0/3 unit 0 family inet address 192.168.2.111/24 vrrp-group 210 accept-data
set interfaces ge-0/0/3 unit 0 family inet address 192.168.2.111/24 vrrp-group 210 advertise-interval 5
set interfaces ge-0/0/3 unit 0 family inet address 192.168.2.111/24 vrrp-group 210 track interface st0 priority-cost 200
FW04
set interfaces ge-0/0/3 unit 0 family inet address 192.168.2.112/24 vrrp-group 210 virtual-address 192.168.2.110
set interfaces ge-0/0/3 unit 0 family inet address 192.168.2.112/24 vrrp-group 210 priority 100
set interfaces ge-0/0/3 unit 0 family inet address 192.168.2.112/24 vrrp-group 210 preempt
set interfaces ge-0/0/3 unit 0 family inet address 192.168.2.112/24 vrrp-group 210 accept-data
set interfaces ge-0/0/3 unit 0 family inet address 192.168.2.112/24 vrrp-group 210 advertise-interval 5
注釈
ファイアウォール(vSRX)のVRRPの切り替わり時間として、Advertise Interval×3回に加え4秒程度必要であるため、Advertise Intervalを5秒に設定した場合、障害発生からトラフィックの切り替わり完了までに19秒程度必要となる想定です。 本設定を変更する場合、先にBackup側のFWから実施してください。Master側を先に変更すると、Backup側へのHelloパケットの送信間隔が変わり、Backup側もMasterに昇格して両装置がMasterになる恐れがあります。
VPN設定(IPsec)
IPsecの設定で利用したパラメータは以下のとおりです。
パラメータ |
値 |
Phase1 |
|
Authentication Method |
Pre-shared key |
Pre-shared key password |
IPSEC_KEY_1 |
DH group |
group14 |
Encryption Algorithm |
AES256-GCM |
ISAKMP SA lifetime |
28800 seconds |
IKE version |
v2-only |
Phase2 |
|
Security protocol |
ESP |
Encryption Algorithm |
AES256-GCM |
IPSEC SA lifetime |
3600 seconds |
perfect-forward-secrecy keys |
group14 |
Establish-tunnel |
immediately |
FW01、02、03、04共通設定
IKEフェーズ1設定
set security ike proposal IKE_PROP1 authentication-method pre-shared-keys
set security ike proposal IKE_PROP1 dh-group group14
set security ike proposal IKE_PROP1 encryption-algorithm aes-256-gcm
set security ike proposal IKE_PROP1 lifetime-seconds 28800
set security ike policy IKE_POL1 mode main
set security ike policy IKE_POL1 proposals IKE_PROP1
set security ike policy IKE_POL1 pre-shared-key ascii-text IPSEC_KEY_1
IKEフェーズ2設定
set security ipsec proposal IPSEC_PROP1 protocol esp
set security ipsec proposal IPSEC_PROP1 encryption-algorithm aes-256-gcm
set security ipsec proposal IPSEC_PROP1 lifetime-seconds 3600
set security ipsec policy IPSEC_POL1 perfect-forward-secrecy keys group14
set security ipsec policy IPSEC_POL1 proposals IPSEC_PROP1
FW01 サイト間接続の設定
set security ike gateway GW1 ike-policy IKE_POL1
set security ike gateway GW1 address 203.0.113.3
set security ike gateway GW1 dead-peer-detection optimized
set security ike gateway GW1 dead-peer-detection interval 10
set security ike gateway GW1 dead-peer-detection threshold 5
set security ike gateway GW1 external-interface lo0
set security ike gateway GW1 version v2-only
set security ipsec vpn VPN1 bind-interface st0.0
set security ipsec vpn VPN1 ike gateway GW1
set security ipsec vpn VPN1 ike ipsec-policy IPSEC_POL1
set security ipsec vpn VPN1 establish-tunnels immediately
FW02 サイト間接続の設定
set security ike gateway GW1 ike-policy IKE_POL1
set security ike gateway GW1 address 203.0.113.4
set security ike gateway GW1 external-interface lo0
set security ike gateway GW1 version v2-only
set security ipsec vpn VPN1 bind-interface st0.0
set security ipsec vpn VPN1 ike gateway GW1
set security ipsec vpn VPN1 ike ipsec-policy IPSEC_POL1
set security ipsec vpn VPN1 establish-tunnels immediately
FW03 サイト間接続の設定
set security ike gateway GW1 ike-policy IKE_POL1
set security ike gateway GW1 address 203.0.113.1
set security ike gateway GW1 dead-peer-detection optimized
set security ike gateway GW1 dead-peer-detection interval 10
set security ike gateway GW1 dead-peer-detection threshold 5
set security ike gateway GW1 external-interface lo0
set security ike gateway GW1 version v2-only
set security ipsec vpn VPN1 bind-interface st0.0
set security ipsec vpn VPN1 ike gateway GW1
set security ipsec vpn VPN1 ike ipsec-policy IPSEC_POL1
set security ipsec vpn VPN1 establish-tunnels immediately
FW04 サイト間接続の設定
set security ike gateway GW1 ike-policy IKE_POL1
set security ike gateway GW1 address 203.0.113.2
set security ike gateway GW1 external-interface lo0
set security ike gateway GW1 version v2-only
set security ipsec vpn VPN1 bind-interface st0.0
set security ipsec vpn VPN1 ike gateway GW1
set security ipsec vpn VPN1 ike ipsec-policy IPSEC_POL1
set security ipsec vpn VPN1 establish-tunnels immediately
注釈
FW01、03では、IPsec対向装置間で通信障害が発生した場合、異常を検知し切り替えを実行するためのDead Peer Detection(以下DPD)の設定をしています。 DPDのモードである「optimized」は最後にIPsecトンネルを通過した通信から戻りの通信が無い場合に、DPDによる監視をスタートさせる設定です。 製品仕様上、監視パラメータのインターバルが10秒、閾値が5回となっているので、回線断の検知と切り替え完了まで1分程度の時間がかかります。
ルーティング設定
FW01
set routing-options static route 192.168.2.0/24 next-hop st0.0
set routing-options static route 0.0.0.0/0 next-hop 10.0.10.254
FW02
set routing-options static route 192.168.2.0/24 next-hop st0.0
set routing-options static route 0.0.0.0/0 next-hop 10.0.10.254
FW03
set routing-options static route 192.168.1.0/24 next-hop st0.0
set routing-options static route 0.0.0.0/0 next-hop 10.0.20.254
FW04
set routing-options static route 192.168.1.0/24 next-hop st0.0
set routing-options static route 0.0.0.0/0 next-hop 10.0.20.254
設定内容の確認
前述の設定が正しく投入されている場合、以下の出力を確認できます。
FW01
user@FW01> show configuration | no-more
(中略)
security {
ike {
proposal IKE_PROP1 {
authentication-method pre-shared-keys;
dh-group group14;
encryption-algorithm aes-256-gcm;
lifetime-seconds 28800;
}
policy IKE_POL1 {
mode main;
proposals IKE_PROP1;
pre-shared-key ascii-text "$9$YDgaGUjkPTFCtOIcl8L2goJGjTznu1En6"; ## SECRET-DATA
}
gateway GW1 {
ike-policy IKE_POL1;
address 203.0.113.3;
dead-peer-detection {
always-send;
interval 10;
threshold 5;
}
external-interface lo0;
version v2-only;
}
}
ipsec {
proposal IPSEC_PROP1 {
protocol esp;
encryption-algorithm aes-256-gcm;
lifetime-seconds 3600;
}
policy IPSEC_POL1 {
perfect-forward-secrecy {
keys group14;
}
proposals IPSEC_PROP1;
}
vpn VPN1 {
bind-interface st0.0;
ike {
gateway GW1;
ipsec-policy IPSEC_POL1;
}
establish-tunnels immediately;
}
}
address-book {
global {
address LOCAL_LAN 192.168.1.0/24;
address REMOTE_LAN 192.168.2.0/24;
}
}
policies {
from-zone trust to-zone trust {
policy default-permit {
match {
source-address any;
destination-address any;
application any;
}
then {
permit;
}
}
}
from-zone trust to-zone untrust {
policy default-permit {
match {
source-address any;
destination-address any;
application any;
}
then {
permit;
}
}
}
from-zone untrust to-zone trust {
policy fromIPSEC {
match {
source-address REMOTE_LAN;
destination-address LOCAL_LAN;
application any;
}
then {
permit;
}
}
policy DENY-ALL {
match {
source-address any;
destination-address any;
application any;
}
then {
deny;
}
}
}
}
zones {
security-zone trust {
tcp-rst;
interfaces {
ge-0/0/0.0 {
host-inbound-traffic {
system-services {
ssh;
ping;
}
}
}
ge-0/0/2.0 {
host-inbound-traffic {
system-services {
all;
}
protocols {
vrrp;
}
}
}
}
}
security-zone untrust {
screen untrust-screen;
interfaces {
ge-0/0/1.0;
lo0.0 {
host-inbound-traffic {
system-services {
ike;
}
}
}
st0.0;
}
}
}
}
interfaces {
ge-0/0/1 {
unit 0 {
family inet {
address 10.0.10.101/24;
}
}
}
ge-0/0/2 {
unit 0 {
family inet {
address 192.168.1.101/24 {
vrrp-group 100 {
virtual-address 192.168.1.100;
priority 200;
advertise-interval 5;
preempt;
accept-data;
track {
interface st0 {
priority-cost 200;
}
}
}
}
}
}
}
lo0 {
unit 0 {
family inet {
address 203.0.113.1/32;
}
}
}
st0 {
unit 0 {
family inet {
address 10.1.1.101/24;
}
}
}
}
routing-options {
static {
route 192.168.2.0/24 next-hop st0.0;
route 0.0.0.0/0 next-hop 10.0.10.254;
}
}
user@FW01>
FW02
user@FW02> show configuration | no-more
(中略)
security {
ike {
proposal IKE_PROP1 {
authentication-method pre-shared-keys;
dh-group group14;
encryption-algorithm aes-256-gcm;
lifetime-seconds 28800;
}
policy IKE_POL1 {
mode main;
proposals IKE_PROP1;
pre-shared-key ascii-text "$9$L.Vx-bwY4ZDHfT3/tOhcXxNdbYDiqz6C
}
gateway GW1 {
ike-policy IKE_POL1;
address 203.0.113.4;
external-interface lo0;
version v2-only;
}
}
ipsec {
proposal IPSEC_PROP1 {
protocol esp;
encryption-algorithm aes-256-gcm;
lifetime-seconds 3600;
}
policy IPSEC_POL1 {
perfect-forward-secrecy {
keys group14;
}
proposals IPSEC_PROP1;
}
vpn VPN1 {
bind-interface st0.0;
ike {
gateway GW1;
ipsec-policy IPSEC_POL1;
}
establish-tunnels immediately;
}
}
address-book {
global {
address LOCAL_LAN 192.168.1.0/24;
address REMOTE_LAN 192.168.2.0/24;
}
}
policies {
from-zone trust to-zone trust {
policy default-permit {
match {
source-address any;
destination-address any;
application any;
}
then {
permit;
}
}
}
from-zone trust to-zone untrust {
policy default-permit {
match {
source-address any;
destination-address any;
application any;
}
then {
permit;
}
}
}
from-zone untrust to-zone trust {
policy fromIPSEC {
match {
source-address REMOTE_LAN;
destination-address LOCAL_LAN;
application any;
}
then {
permit;
}
}
policy DENY-ALL {
match {
source-address any;
destination-address any;
application any;
}
then {
deny;
}
}
}
}
zones {
security-zone trust {
tcp-rst;
interfaces {
ge-0/0/0.0 {
host-inbound-traffic {
system-services {
ssh;
ping;
}
}
}
ge-0/0/2.0 {
host-inbound-traffic {
system-services {
all;
}
protocols {
vrrp;
}
}
}
}
}
security-zone untrust {
screen untrust-screen;
interfaces {
ge-0/0/1.0;
lo0.0 {
host-inbound-traffic {
system-services {
ike;
}
}
}
st0.0;
}
}
}
}
interfaces {
ge-0/0/1 {
unit 0 {
family inet {
address 10.0.10.102/24;
}
}
}
ge-0/0/2 {
unit 0 {
family inet {
address 192.168.1.102/24 {
vrrp-group 100 {
virtual-address 192.168.1.100;
priority 100;
advertise-interval 5;
preempt;
accept-data;
}
}
}
}
}
lo0 {
unit 0 {
family inet {
address 203.0.113.2/32;
}
}
}
st0 {
unit 0 {
family inet {
address 10.1.2.102/24;
}
}
}
}
routing-options {
static {
route 192.168.2.0/24 next-hop st0.0;
route 0.0.0.0/0 next-hop 10.0.10.254;
}
}
user@FW02>
FW03
user@FW03> show configuration | no-more
(中略)
security {
ike {
proposal IKE_PROP1 {
authentication-method pre-shared-keys;
dh-group group14;
encryption-algorithm aes-256-gcm;
lifetime-seconds 28800;
}
policy IKE_POL1 {
mode main;
proposals IKE_PROP1;
pre-shared-key ascii-text "$9$JxGjkqm5F6CO1
}
gateway GW1 {
ike-policy IKE_POL1;
address 203.0.113.1;
dead-peer-detection {
optimized;
interval 10;
threshold 5;
}
external-interface lo0;
version v2-only;
}
}
ipsec {
proposal IPSEC_PROP1 {
protocol esp;
encryption-algorithm aes-256-gcm;
lifetime-seconds 3600;
}
policy IPSEC_POL1 {
perfect-forward-secrecy {
keys group14;
}
proposals IPSEC_PROP1;
}
vpn VPN1 {
bind-interface st0.0;
ike {
gateway GW1;
ipsec-policy IPSEC_POL1;
}
establish-tunnels immediately;
}
}
address-book {
global {
address LOCAL_LAN 192.168.2.0/24;
address REMOTE_LAN 192.168.1.0/24;
}
}
policies {
from-zone trust to-zone trust {
policy default-permit {
match {
source-address any;
destination-address any;
application any;
}
then {
permit;
}
}
}
from-zone trust to-zone untrust {
policy default-permit {
match {
source-address any;
destination-address any;
application any;
}
then {
permit;
}
}
}
from-zone untrust to-zone trust {
policy fromIPSEC {
match {
source-address REMOTE_LAN;
destination-address LOCAL_LAN;
application any;
}
then {
permit;
}
}
policy DENY-ALL {
match {
source-address any;
destination-address any;
application any;
}
then {
deny;
}
}
}
}
zones {
security-zone trust {
tcp-rst;
interfaces {
ge-0/0/0.0 {
host-inbound-traffic {
system-services {
ssh;
ping;
}
}
}
ge-0/0/3.0 {
host-inbound-traffic {
system-services {
all;
}
protocols {
vrrp;
}
}
}
}
}
security-zone untrust {
screen untrust-screen;
interfaces {
ge-0/0/1.0;
lo0.0 {
host-inbound-traffic {
system-services {
ike;
}
}
}
st0.0;
}
}
}
}
interfaces {
ge-0/0/1 {
unit 0 {
family inet {
address 10.0.20.111/24;
}
}
}
ge-0/0/3 {
unit 0 {
family inet {
address 192.168.2.111/24 {
vrrp-group 210 {
virtual-address 192.168.2.110;
priority 200;
advertise-interval 5;
preempt;
accept-data;
track {
interface st0 {
priority-cost 200;
}
}
}
}
}
}
}
lo0 {
unit 0 {
family inet {
address 203.0.113.3/32;
}
}
}
st0 {
unit 0 {
family inet {
address 10.1.1.111/24;
}
}
}
}
routing-options {
static {
route 192.168.1.0/24 next-hop st0.0;
route 0.0.0.0/0 next-hop 10.0.20.254;
}
}
user@FW03>
FW04
user@FW04> show configuration | no-more
(中略)
security {
ike {
proposal IKE_PROP1 {
authentication-method pre-shared-keys;
dh-group group14;
encryption-algorithm aes-256-gcm;
lifetime-seconds 28800;
}
policy IKE_POL1 {
mode main;
proposals IKE_PROP1;
pre-shared-key ascii-text "$9$-CVsg4aGiqPFnCpBEledVwYgaqm5/t05T"; ## SECRET-DATA
}
gateway GW1 {
ike-policy IKE_POL1;
address 203.0.113.2;
external-interface lo0;
version v2-only;
}
}
ipsec {
proposal IPSEC_PROP1 {
protocol esp;
encryption-algorithm aes-256-gcm;
lifetime-seconds 3600;
}
policy IPSEC_POL1 {
perfect-forward-secrecy {
keys group14;
}
proposals IPSEC_PROP1;
}
vpn VPN1 {
bind-interface st0.0;
ike {
gateway GW1;
ipsec-policy IPSEC_POL1;
}
establish-tunnels immediately;
}
}
address-book {
global {
address LOCAL_LAN 192.168.2.0/24;
address REMOTE_LAN 192.168.1.0/24;
}
}
policies {
from-zone trust to-zone trust {
policy default-permit {
match {
source-address any;
destination-address any;
application any;
}
then {
permit;
}
}
}
from-zone trust to-zone untrust {
policy default-permit {
match {
source-address any;
destination-address any;
application any;
}
then {
permit;
}
}
}
from-zone untrust to-zone trust {
policy fromIPSEC {
match {
source-address REMOTE_LAN;
destination-address LOCAL_LAN;
application any;
}
then {
permit;
}
}
policy DENY-ALL {
match {
source-address any;
destination-address any;
application any;
}
then {
deny;
}
}
}
}
zones {
security-zone trust {
tcp-rst;
interfaces {
ge-0/0/0.0 {
host-inbound-traffic {
system-services {
ssh;
ping;
}
}
}
ge-0/0/3.0 {
host-inbound-traffic {
system-services {
all;
}
protocols {
vrrp;
}
}
}
}
}
security-zone untrust {
screen untrust-screen;
interfaces {
ge-0/0/1.0;
lo0.0 {
host-inbound-traffic {
system-services {
ike;
}
}
}
st0.0;
}
}
}
}
interfaces {
ge-0/0/1 {
unit 0 {
family inet {
address 10.0.20.112/24;
}
}
}
ge-0/0/3 {
unit 0 {
family inet {
address 192.168.2.112/24 {
vrrp-group 210 {
virtual-address 192.168.2.110;
priority 100;
advertise-interval 5;
preempt;
accept-data;
}
}
}
}
}
lo0 {
unit 0 {
family inet {
address 203.0.113.4/32;
}
}
}
st0 {
unit 0 {
family inet {
address 10.1.2.112/24;
}
}
}
}
routing-options {
static {
route 192.168.1.0/24 next-hop st0.0;
route 0.0.0.0/0 next-hop 10.0.20.254;
}
}
user@FW04>
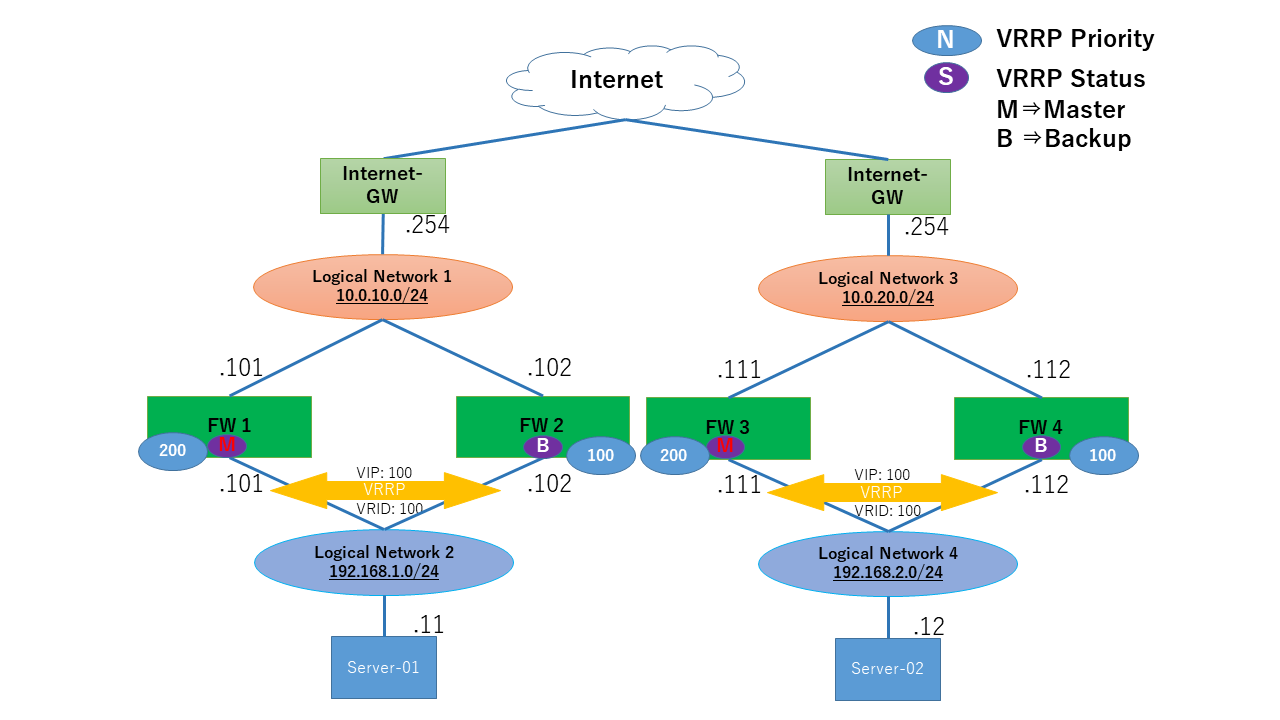
1.6.3. 通信の流れ¶
Server-01、02は正常時、MasterであるFW01、03を通して通信します。
正常通信時の状態確認
正常通信時のFWの状態は以下のように確認できます。
VRRPの状態
FW01がMasterであることを確認できます。
user@FW01> show vrrp
Interface State Group VR state VR Mode Timer Type Address
ge-0/0/2.0 up 100 master Active A 7.054 lcl 192.168.1.101
vip 192.168.1.100
FW02がBackupであることを確認できます。
user@FW02> show vrrp
Interface State Group VR state VR Mode Timer Type Address
ge-0/0/2.0 up 100 backup Active D 43.961lcl 192.168.1.102
vip 192.168.1.100
mas 192.168.1.101
FW03がMasterであることを確認できます。
user@FW03> show vrrp
Interface State Group VR state VR Mode Timer Type Address
ge-0/0/3.0 up 210 master Active A 0.089 lcl 192.168.2.111
vip 192.168.2.110
FW04がBackupであることを確認できます。
user@FW04> show vrrp
Interface State Group VR state VR Mode Timer Type Address
ge-0/0/3.0 up 210 backup Active D 59.190lcl 192.168.2.112
vip 192.168.2.110
mas 192.168.2.111
Interface State Group VR state VR Mode Timer Type Address
ge-0/0/3.0 up 210 master Active A 0.089 lcl 192.168.2.111
vip 192.168.2.110
FW01とFW03がIPsecトンネルを確立していることを確認できます。
user@FW01> show security ipsec sa
Total active tunnels: 1
ID Algorithm SPI Life:sec/kb Mon lsys Port Gateway
<131073 ESP:aes-gcm-256/None fff55e05 3540/ unlim - root 500 203.0.113.3
>131073 ESP:aes-gcm-256/None ffe1b571 3540/ unlim - root 500 203.0.113.3
user@FW01> show security ike security-associations
Index State Initiator cookie Responder cookie Mode Remote Address
1843545 UP 8dd5917ee3e9df05 230269c4740c7322 IKEv2 203.0.113.3
user@FW03> show security ipsec sa
Total active tunnels: 1 Total Ipsec sas: 1
ID Algorithm SPI Life:sec/kb Mon lsys Port Gateway
<131073 ESP:aes-gcm-256/None ffe1b571 3550/ unlim - root 500 203.0.113.1
>131073 ESP:aes-gcm-256/None fff55e05 3550/ unlim - root 500 203.0.113.1
user@FW03> show security ike security-associations
Index State Initiator cookie Responder cookie Mode Remote Address
680470 UP 8dd5917ee3e9df05 230269c4740c7322 IKEv2 203.0.113.1
FW02とFW04がIPsecトンネルを確立していることを確認できます。
user@FW02> show security ipsec sa
Total active tunnels: 1
ID Algorithm SPI Life:sec/kb Mon lsys Port Gateway
<131073 ESP:aes-gcm-256/None 2d15959d 1344/ unlim - root 500 203.0.113.4
>131073 ESP:aes-gcm-256/None 974f8684 1344/ unlim - root 500 203.0.113.4
user@FW02> show security ike security-associations
Index State Initiator cookie Responder cookie Mode Remote Address
680506 UP c595944e6ff1abfe edbbad006ef0f384 IKEv2 203.0.113.4
user@FW04> show security ipsec sa
Total active tunnels: 1 Total Ipsec sas: 1
ID Algorithm SPI Life:sec/kb Mon lsys Port Gateway
<131073 ESP:aes-gcm-256/None 974f8684 1346/ unlim - root 500 203.0.113.2
>131073 ESP:aes-gcm-256/None 2d15959d 1346/ unlim - root 500 203.0.113.2
user@FW04> show security ike security-associations
Index State Initiator cookie Responder cookie Mode Remote Address
6085344 UP a8f83271c302524c 80fefc81bb10c935 IKEv2 203.0.113.2
インターフェイスの状態
FW01のVPNトンネルインターフェイス(st)がUPしていることを確認できます。
user@FW01> show interfaces terse | no-more
Interface Admin Link Proto Local Remote
ge-0/0/1 up up
ge-0/0/1.0 up up inet 10.0.10.101/24
ge-0/0/2 up up
ge-0/0/2.0 up up inet 192.168.1.100/24
192.168.1.101/24
(中略)
lo0 up up
lo0.0 up up inet 203.0.113.1 --> 0/0
(中略)
st0 up up
st0.0 up up inet 10.1.1.101/24
user@FW01>
FW02のVPNトンネルインターフェイス(st)がUPしていることを確認できます。
user@FW02> show interfaces terse | no-more
Interface Admin Link Proto Local Remote
ge-0/0/1 up up
ge-0/0/1.0 up up inet 10.0.10.102/24
ge-0/0/2 up up
ge-0/0/2.0 up up inet 192.168.1.102/24
(中略)
lo0 up up
lo0.0 up up inet 203.0.113.2 --> 0/0
(中略)
st0 up up
st0.0 up up inet 10.1.2.102/24
user@FW02>
FW03のVPNトンネルインターフェイス(st)がUPしていることを確認できます。
user@FW03> show interfaces terse | no-more
Interface Admin Link Proto Local Remote
ge-0/0/1 up up
ge-0/0/1.0 up up inet 10.0.20.111/24
ge-0/0/2 down down
ge-0/0/3 up up
ge-0/0/3.0 up up inet 192.168.2.110/24
192.168.2.111/24
(中略)
lo0 up up
lo0.0 up up inet 203.0.113.3 --> 0/0
(中略)
st0 up up
st0.0 up up inet 10.1.1.111/24
user@FW03>
FW04のVPNトンネルインターフェイス(st)がUPしていることを確認できます。
user@FW04> show interfaces terse | no-more
Interface Admin Link Proto Local Remote
ge-0/0/1 up up
ge-0/0/1.0 up up inet 10.0.20.112/24
ge-0/0/2 down down
ge-0/0/3 up up
ge-0/0/3.0 up up inet 192.168.2.112/24
(中略)
lo0 up up
lo0.0 up up inet 203.0.113.4 --> 0/0
(中略)
st0 up up
st0.0 up up inet 10.1.1.111/24
user@FW04>
ルーティングの状態
FW01の拠点A(192.168.2.0/24)に対するルートがVPNトンネルインターフェイス(st)に向いていることを確認できます。
user@FW01> show route
inet.0: 15 destinations, 15 routes (15 active, 0 holddown, 0 hidden)
+ = Active Route, - = Last Active, * = Both
0.0.0.0/0 *[Static/5] 1w0d 07:33:21
> to 10.0.10.254 via ge-0/0/1.0
10.0.0.0/24 *[Direct/0] 1w0d 11:16:11
> via ge-0/0/0.0
10.0.0.101/32 *[Local/0] 1w0d 11:16:11
Local via ge-0/0/0.0
10.0.10.0/24 *[Direct/0] 1w0d 07:33:21
> via ge-0/0/1.0
10.0.10.101/32 *[Local/0] 1w0d 11:16:11
Local via ge-0/0/1.0
10.1.1.0/24 *[Direct/0] 1w0d 07:33:11
> via st0.0
10.1.1.101/32 *[Local/0] 1w0d 10:21:15
Local via st0.0
(中略)
192.168.1.0/24 *[Direct/0] 1w0d 07:33:21
> via ge-0/0/2.0
192.168.1.100/32 *[Local/0] 1w0d 07:32:10
Local via ge-0/0/2.0
192.168.1.101/32 *[Local/0] 1w0d 11:16:11
Local via ge-0/0/2.0
192.168.2.0/24 *[Static/5] 1w0d 07:33:11
> via st0.0
user@FW01>
FW02の拠点A(192.168.2.0/24)に対するルートがVPNトンネルインターフェイス(st)に向いていることを確認できます。
user@FW02> show route
inet.0: 14 destinations, 14 routes (14 active, 0 holddown, 0 hidden)
+ = Active Route, - = Last Active, * = Both
0.0.0.0/0 *[Static/5] 1w0d 09:25:08
> to 10.0.10.254 via ge-0/0/1.0
10.0.0.0/24 *[Direct/0] 1w0d 11:14:24
> via ge-0/0/0.0
10.0.0.102/32 *[Local/0] 1w0d 11:14:24
Local via ge-0/0/0.0
10.0.10.0/24 *[Direct/0] 1w0d 11:14:24
> via ge-0/0/1.0
10.0.10.102/32 *[Local/0] 1w0d 11:14:24
Local via ge-0/0/1.0
10.1.2.0/24 *[Direct/0] 00:11:35
> via st0.0
10.1.2.102/32 *[Local/0] 1w0d 10:18:14
Local via st0.0
(中略)
192.168.1.0/24 *[Direct/0] 1w0d 08:55:13
> via ge-0/0/2.0
192.168.1.102/32 *[Local/0] 1w0d 11:14:24
Local via ge-0/0/2.0
192.168.2.0/24 *[Static/5] 00:11:35
> via st0.0
user@FW02>
FW03の拠点A(192.168.1.0/24)に対するルートがVPNトンネルインターフェイス(st)に向いていることを確認できます。
user@FW03> show route
inet.0: 15 destinations, 15 routes (15 active, 0 holddown, 0 hidden)
+ = Active Route, - = Last Active, * = Both
0.0.0.0/0 *[Static/5] 1w0d 09:47:18
> to 10.0.20.254 via ge-0/0
10.0.0.0/24 *[Direct/0] 1w0d 11:12:43
> via ge-0/0/0.0
10.0.0.111/32 *[Local/0] 1w0d 11:12:43
Local via ge-0/0/0.0
10.0.20.0/24 *[Direct/0] 1w0d 10:09:11
> via ge-0/0/1.0
10.0.20.111/32 *[Local/0] 1w0d 10:09:11
Local via ge-0/0/1.0
10.1.1.0/24 *[Direct/0] 1w0d 07:33:17
> via st0.0
10.1.1.111/32 *[Local/0] 1w0d 07:33:17
Local via st0.0
(中略)
192.168.1.0/24 *[Static/5] 1w0d 07:33:17
> via st0.0
192.168.2.0/24 *[Direct/0] 1w0d 10:09:10
> via ge-0/0/3.0
192.168.2.110/32 *[Local/0] 1w0d 07:33:01
Local via ge-0/0/3.0
192.168.2.111/32 *[Local/0] 1w0d 10:09:10
Local via ge-0/0/3.0
user@FW03>
FW04の拠点A(192.168.1.0/24)に対するルートがVPNトンネルインターフェイス(st)に向いていることを確認できます。
user@FW04> show route
inet.0: 15 destinations, 15 routes (15 active, 0 holddown, 0 hidden)
+ = Active Route, - = Last Active, * = Both
0.0.0.0/0 *[Static/5] 1w0d 09:25:35
> to 10.0.20.254 via ge-0/0/1.0
10.0.0.0/24 *[Direct/0] 1w0d 11:01:45
> via ge-0/0/0.0
10.0.0.112/32 *[Local/0] 1w0d 11:01:45
Local via ge-0/0/0.0
10.0.20.0/24 *[Direct/0] 1w0d 11:01:45
> via ge-0/0/1.0
10.0.20.112/32 *[Local/0] 1w0d 11:01:45
Local via ge-0/0/1.0
10.1.2.0/24 *[Direct/0] 1w0d 09:24:43
> via st0.0
10.1.2.112/32 *[Local/0] 1w0d 09:24:43
Local via st0.0
(中略)
192.168.1.0/24 *[Static/5] 1w0d 09:24:43
> via st0.0
192.168.2.0/24 *[Direct/0] 1w0d 11:01:45
> via ge-0/0/3.0
192.168.2.112/32 *[Local/0] 1w0d 11:01:45
Local via ge-0/0/3.0
user@FW04>
サーバーの接続確認
ping、HTTP通信が正常(OK)であることを確認します。
Server-01
pingコマンドを用いて通信を確認します。
[root@Server-01 ~]# ping -c 5 192.168.2.12
PING 192.168.2.12 (192.168.2.12) 56(84) bytes of data.
64 bytes from 192.168.2.12: icmp_seq=1 ttl=62 time=7.02 ms
64 bytes from 192.168.2.12: icmp_seq=2 ttl=62 time=1.45 ms
64 bytes from 192.168.2.12: icmp_seq=3 ttl=62 time=1.34 ms
64 bytes from 192.168.2.12: icmp_seq=4 ttl=62 time=3.01 ms
64 bytes from 192.168.2.12: icmp_seq=5 ttl=62 time=1.93 ms
--- 192.168.2.12 ping statistics ---
5 packets transmitted, 5 received, 0% packet loss, time 4005ms
rtt min/avg/max/mdev = 1.346/2.953/7.024/2.119 ms
[root@server-01 ~]#
Server-02
pingコマンドを用いて通信を確認します。
[root@Server-02 ~]# ping -c 5 192.168.1.11
PING 192.168.1.11 (192.168.1.11) 56(84) bytes of data.
64 bytes from 192.168.1.11: icmp_seq=1 ttl=62 time=4.81 ms
curl -i http://192.168.1.11
64 bytes from 192.168.1.11: icmp_seq=2 ttl=62 time=1.66 ms
64 bytes from 192.168.1.11: icmp_seq=3 ttl=62 time=1.56 ms
64 bytes from 192.168.1.11: icmp_seq=4 ttl=62 time=1.56 ms
64 bytes from 192.168.1.11: icmp_seq=5 ttl=62 time=1.52 ms
--- 192.168.1.11 ping statistics ---
5 packets transmitted, 5 received, 0% packet loss, time 4007ms
rtt min/avg/max/mdev = 1.528/2.226/4.815/1.296 ms
[root@Server-02 ~]#
curlコマンドを用いてHTTP通信を確認します。
[root@Server-02 ~]# curl -i http://192.168.1.11
HTTP/1.1 200 OK
Date: Tue, 03 Mar 2020 11:51:00 GMT
Server: Apache/2.4.6 (CentOS)
Last-Modified: Fri, 07 Feb 2020 05:46:48 GMT
ETag: "7d-59df5ea63a394"
Accept-Ranges: bytes
Content-Length: 125
Content-Type: text/html; charset=UTF-8
<html>
<head><title>IPsec-site-to-site</title></head>
<body>
<p>Web Server01 test page</p>
</body>
</html>
[root@Server-02 ~]#
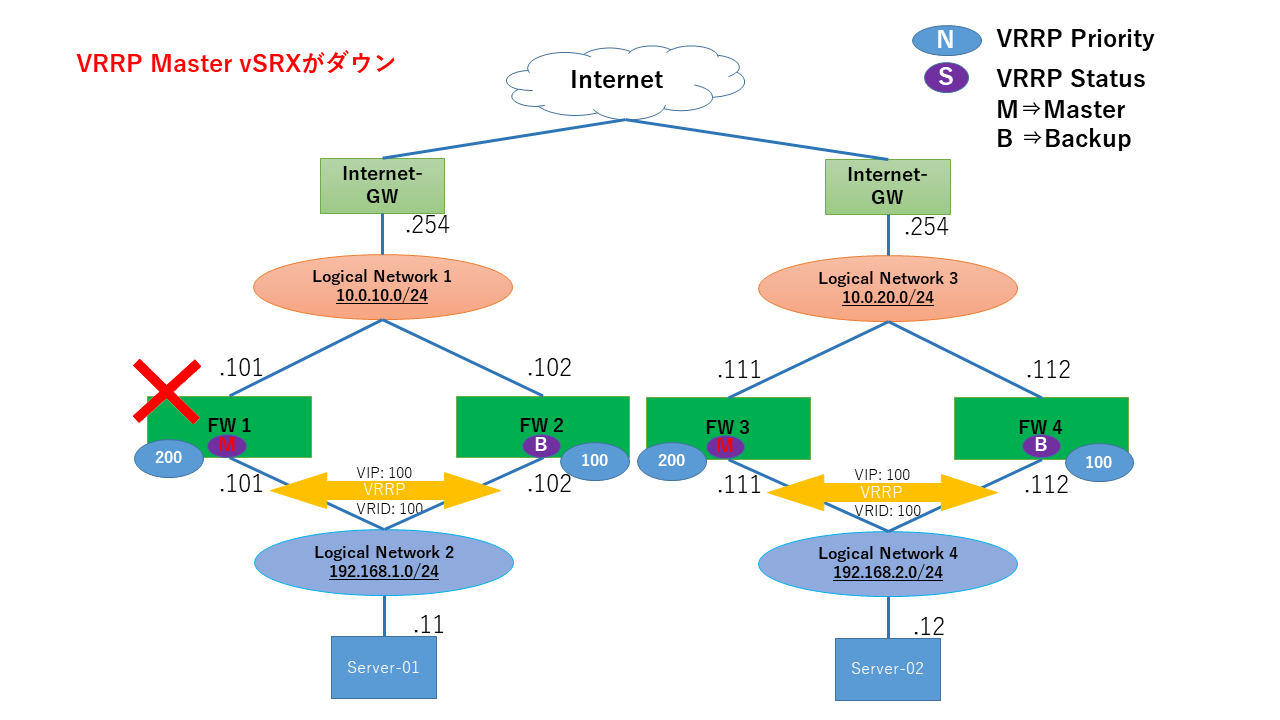
1.6.4. 障害発生時の通信の流れ¶
FW01にインスタンス障害が発生した場合、Server-01、02 はFW02、04を通してインターネットゲートウェイへ通信します。
注釈
FW03がDPDで異常を検知して切り替えが完了するまでに1分程度の時間がかかります。 インスタンス障害の試験方法として、FW01のインターフェイスを一時的に無効化する手法を採用しています。
任意のインターフェイスを無効化/有効化するコマンドは以下のとおりです。
無効化
# set interfaces [INTERFACE NAME] disable
有効化
# delete interfaces [INTERFACE NAME] disable
例
インターフェイス無効化の設定コマンド
# set interfaces ge-0/0/1.0 disable
# set interfaces ge-0/0/2.0 disable
インターフェイス有効化の設定コマンド
# delete interfaces ge-0/0/1.0 disable
# delete interfaces ge-0/0/2.0 disable
障害発生時の状態確認
障害発生時のFWの状態は以下のように確認できます。
VRRPの状態
FW01がMasterでないことを確認できます。
user@FW01> show vrrp
Interface State Group VR state VR Mode Timer Type Address
ge-0/0/2.0 down 100 init Active N 0.000 lcl 192.168.1.101
vip 192.168.1.100
注釈
インターフェイスの無効化によりMasterが切り替わります。
FW02がMasterであることを確認できます。
user@FW02> show vrrp
Interface State Group VR state VR Mode Timer Type Address
ge-0/0/2.0 up 100 master Active A 4.238 lcl 192.168.1.102
vip 192.168.1.100
FW03がMasterでないことを確認できます。
user@FW03> show vrrp
Interface State Group VR state VR Mode Timer Type Address
ge-0/0/3.0 up 210 idle Active N 0.000 lcl 192.168.2.111
vip 192.168.2.110
注釈
FW01が障害によりMasterでなくなっているためTracking機能によりMasterがFW03から切り替わっていることを確認できます。
FW04がMasterであることを確認できます。
user@FW04> show vrrp
Interface State Group VR state VR Mode Timer Type Address
ge-0/0/3.0 up 210 master Active A 5.540 lcl 192.168.2.112
vip 192.168.2.110
トンネルの状態
FW01とFW03がIPsecトンネルを確立していないことを確認できます。
user@FW01> show security ike security-associations
user@FW01> show security ipsec statistics
ESP Statistics:
Encrypted bytes: 7388
Decrypted bytes: 4344
Encrypted packets: 51
Decrypted packets: 53
AH Statistics:
Input bytes: 0
Output bytes: 0
Input packets: 0
Output packets: 0
Errors:
AH authentication failures: 0, Replay errors: 0
ESP authentication failures: 0, ESP decryption failures: 0
Bad headers: 0, Bad trailers: 0
user@FW03> show security ike security-associations
user@FW03> show security ipsec statistics
ESP Statistics:
Encrypted bytes: 74480
Decrypted bytes: 34944
Encrypted packets: 532
Decrypted packets: 416
AH Statistics:
Input bytes: 0
Output bytes: 0
Input packets: 0
Output packets: 0
Errors:
AH authentication failures: 0, Replay errors: 0
ESP authentication failures: 0, ESP decryption failures: 0
Bad headers: 0, Bad trailers: 0
FW02とFW04がVPNを確立していることを確認できます。
user@FW02> show security ipsec sa
Total active tunnels: 1
ID Algorithm SPI Life:sec/kb Mon lsys Port Gateway
<131073 ESP:aes-gcm-256/None 2d15959d 630/ unlim - root 500 203.0.113.4
>131073 ESP:aes-gcm-256/None 974f8684 630/ unlim - root 500 203.0.113.4
user@FW02> show security ike security-associations
Index State Initiator cookie Responder cookie Mode Remote Address
65310 UP 4594bf121c16ab50 8df20587eef88dda IKEv2 203.0.113.4
user@FW04> show security ipsec sa
Total active tunnels: 1
ID Algorithm SPI Life:sec/kb Mon lsys Port Gateway
<131073 ESP:aes-gcm-256/None 974f8684 652/ unlim - root 500 203.0.113.2
>131073 ESP:aes-gcm-256/None 2d15959d 652/ unlim - root 500 203.0.113.2
user@FW04> show security ike security-associations
Index State Initiator cookie Responder cookie Mode Remote Address
6085259 UP 4594bf121c16ab50 8df20587eef88dda IKEv2 203.0.113.2
インターフェイスの状態
FW01のVPNトンネルインターフェイス(st)がDOWNしていることを確認できます。
user@FW01> show interfaces terse | no-more
Interface Admin Link Proto Local Remote
ge-0/0/1 up up
ge-0/0/1.0 up up inet 10.0.10.101/24
ge-0/0/2 up up
ge-0/0/2.0 up up inet 192.168.1.100/24
192.168.1.101/24
(中略)
lo0 up up
lo0.0 up up inet 203.0.113.1 --> 0/0
(中略)
st0 up up
st0.0 up down inet 10.1.1.101/24
user@FW01>
FW02のVPNトンネルインターフェイス(st)がUPしていることを確認できます。
user@FW02> show interfaces terse | no-more
Interface Admin Link Proto Local Remote
ge-0/0/1 up up
ge-0/0/1.0 up up inet 10.0.10.102/24
ge-0/0/2 up up
ge-0/0/2.0 up up inet 192.168.1.100/24
192.168.1.102/24
(中略)
lo0 up up
lo0.0 up up inet 203.0.113.2 --> 0/0
(中略)
st0 up up
st0.0 up up inet 10.1.2.102/24
user@FW02>
FW03のVPNトンネルインターフェイス(st)がDOWNしていることを確認できます。
user@FW03> show interfaces terse | no-more
Interface Admin Link Proto Local Remote
ge-0/0/1 up up
ge-0/0/1.0 up up inet 10.0.20.111/24
ge-0/0/2 down down
ge-0/0/3 up up
ge-0/0/3.0 up up inet 192.168.2.111/24
(中略)
lo0 up up
lo0.0 up up inet 203.0.113.3 --> 0/0
(中略)
st0 up up
st0.0 up down inet 10.1.1.111/24
user@FW03>
FW04のVPNトンネルインターフェイス(st)がUPしていることを確認できます。
user@FW04> show interfaces terse | no-more
Interface Admin Link Proto Local Remote
ge-0/0/1 up up
ge-0/0/1.0 up up inet 10.0.20.112/24
ge-0/0/2 down down
ge-0/0/3 up up
ge-0/0/3.0 up up inet 192.168.2.112/24
(中略)
lo0 up up
lo0.0 up up inet 203.0.113.4 --> 0/0
(中略)
st0 up up
st0.0 up up inet 10.1.1.111/24
user@FW04>
ルーティングの状態
FW01の拠点A(192.168.2.0/24)に対する経路がVPNトンネルインターフェイス(st)に向いていないことを確認できます。
user@FW01> show route | no-more
inet.0: 9 destinations, 9 routes (9 active, 0 holddown, 0 hidden)
+ = Active Route, - = Last Active, * = Both
10.0.0.0/24 *[Direct/0] 1w0d 11:25:06
> via ge-0/0/0.0
10.0.0.101/32 *[Local/0] 1w0d 11:25:06
Local via ge-0/0/0.0
10.0.10.101/32 *[Local/0] 1w0d 11:25:06
Reject
10.1.1.101/32 *[Local/0] 1w0d 10:30:10
Reject
(中略)
192.168.1.101/32 *[Local/0] 1w0d 11:25:06
Reject
user@FW01>
FW02の拠点A(192.168.2.0/24)に対する経路がVPNトンネルインターフェイス(st)に向いていることを確認できます。
user@FW02> show route | no-more
inet.0: 15 destinations, 15 routes (15 active, 0 holddown, 0 hidden)
+ = Active Route, - = Last Active, * = Both
0.0.0.0/0 *[Static/5] 1w0d 09:35:57
> to 10.0.10.254 via ge-0/0/1.0
10.0.0.0/24 *[Direct/0] 1w0d 11:25:13
> via ge-0/0/0.0
10.0.0.102/32 *[Local/0] 1w0d 11:25:13
Local via ge-0/0/0.0
10.0.10.0/24 *[Direct/0] 1w0d 11:25:13
> via ge-0/0/1.0
10.0.10.102/32 *[Local/0] 1w0d 11:25:13
Local via ge-0/0/1.0
10.1.2.0/24 *[Direct/0] 00:22:24
> via st0.0
10.1.2.102/32 *[Local/0] 1w0d 10:29:03
Local via st0.0
(中略)
192.168.1.0/24 *[Direct/0] 1w0d 09:06:02
> via ge-0/0/2.0
192.168.1.100/32 *[Local/0] 00:03:20
Local via ge-0/0/2.0
192.168.1.102/32 *[Local/0] 1w0d 11:25:13
Local via ge-0/0/2.0
192.168.2.0/24 *[Static/5] 00:22:24
> via st0.0
user@FW02>
FW03の拠点A(192.168.1.0/24)に対する経路がVPNトンネルインターフェイス(st)に向いていないことを確認できます。
user@FW03> show route | no-more
inet.0: 12 destinations, 12 routes (12 active, 0 holddown, 0 hidden)
+ = Active Route, - = Last Active, * = Both
0.0.0.0/0 *[Static/5] 1w0d 09:57:28
> to 10.0.20.254 via ge-0/0/1.0
10.0.0.0/24 *[Direct/0] 1w0d 11:22:53
> via ge-0/0/0.0
10.0.0.111/32 *[Local/0] 1w0d 11:22:53
Local via ge-0/0/0.0
10.0.20.0/24 *[Direct/0] 1w0d 10:19:21
> via ge-0/0/1.0
10.0.20.111/32 *[Local/0] 1w0d 10:19:21
Local via ge-0/0/1.0
10.1.1.111/32 *[Local/0] 00:01:28
Reject
(中略)
192.168.2.0/24 *[Direct/0] 1w0d 10:19:20
> via ge-0/0/3.0
192.168.2.111/32 *[Local/0] 1w0d 10:19:20
Local via ge-0/0/3.0
user@FW03>
FW04の拠点A(192.168.2.0/24)に対する経路がVPNトンネルインターフェイス(st)に向いていることを確認できます。
user@FW04> show route | no-more
inet.0: 15 destinations, 15 routes (15 active, 0 holddown, 0 hidden)
+ = Active Route, - = Last Active, * = Both
0.0.0.0/0 *[Static/5] 1w0d 09:36:22
> to 10.0.20.254 via ge-0/0/1.0
10.0.0.0/24 *[Direct/0] 1w0d 11:12:32
> via ge-0/0/0.0
10.0.0.112/32 *[Local/0] 1w0d 11:12:32
Local via ge-0/0/0.0
10.0.20.0/24 *[Direct/0] 1w0d 11:12:32
> via ge-0/0/1.0
10.0.20.112/32 *[Local/0] 1w0d 11:12:32
Local via ge-0/0/1.0
10.1.2.0/24 *[Direct/0] 1w0d 09:35:30
> via st0.0
10.1.2.112/32 *[Local/0] 1w0d 09:35:30
Local via st0.0
(中略)
192.168.1.0/24 *[Static/5] 1w0d 09:35:30
> via st0.0
192.168.2.0/24 *[Direct/0] 1w0d 11:12:32
> via ge-0/0/3.0
192.168.2.110/32 *[Local/0] 00:03:26
Local via ge-0/0/3.0
192.168.2.112/32 *[Local/0] 1w0d 11:12:32
Local via ge-0/0/3.0
user@FW04>
サーバーの接続確認
ping、HTTP通信が正常(OK)であることを確認します。
Server-01
pingコマンドを用いて通信を確認します。
[root@server-01 ~]# ping -c 5 192.168.2.12
PING 192.168.2.12 (192.168.2.12) 56(84) bytes of data.
64 bytes from 192.168.2.12: icmp_seq=1 ttl=62 time=6.76 ms
64 bytes from 192.168.2.12: icmp_seq=2 ttl=62 time=1.34 ms
64 bytes from 192.168.2.12: icmp_seq=3 ttl=62 time=1.70 ms
64 bytes from 192.168.2.12: icmp_seq=4 ttl=62 time=1.14 ms
--- 192.168.2.12 ping statistics ---
5 packets transmitted, 5 received, 0% packet loss, time 4005ms
rtt min/avg/max/mdev = 1.346/2.953/7.024/2.119 ms
[root@server-01 ~]#
Server-02
pingコマンドを用いて通信を確認します。
[root@server-02 ~]# ping -c 5 192.168.1.11
PING 192.168.1.11 (192.168.1.11) 56(84) bytes of data.
64 bytes from 192.168.1.11: icmp_seq=1 ttl=62 time=4.81 ms
curl -i http://192.168.1.11
64 bytes from 192.168.1.11: icmp_seq=1 ttl=62 time=5.60 ms
64 bytes from 192.168.1.11: icmp_seq=2 ttl=62 time=1.24 ms
64 bytes from 192.168.1.11: icmp_seq=3 ttl=62 time=1.24 ms
64 bytes from 192.168.1.11: icmp_seq=4 ttl=62 time=1.32 ms
--- 192.168.1.11 ping statistics ---
5 packets transmitted, 5 received, 0% packet loss, time 4007ms
rtt min/avg/max/mdev = 1.528/2.226/4.815/1.296 ms
[root@server-02 ~]#
curlコマンドを用いてHTTP通信を確認します。
[root@server-02 ~]# curl -i http://192.168.1.11
HTTP/1.1 200 OK
Date: Tue, 03 Mar 2020 12:03:08 GMT
Server: Apache/2.4.6 (CentOS)
Last-Modified: Fri, 07 Feb 2020 05:46:48 GMT
ETag: "7d-59df5ea63a394"
Accept-Ranges: bytes
Content-Length: 125
Content-Type: text/html; charset=UTF-8
<html>
<head><title>Migration between different versions</title></head>
<body>
<p>Web Server01 test page</p>
</body>
</html>
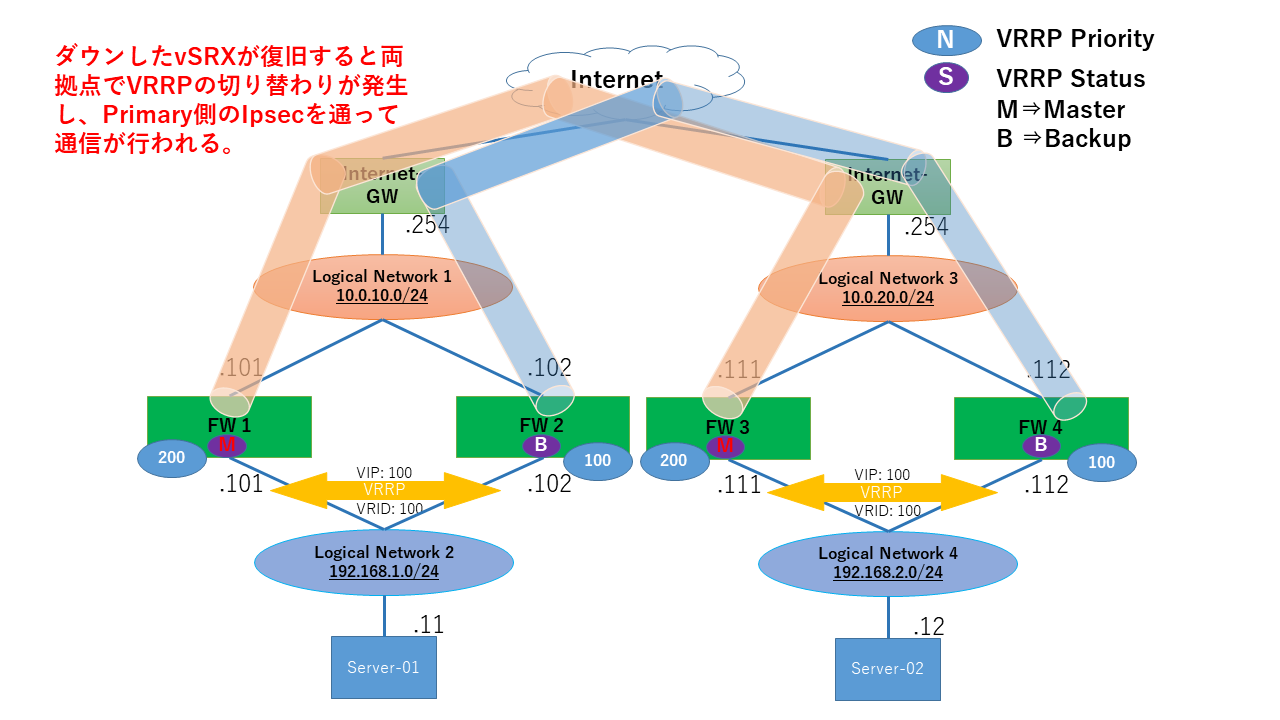
1.6.5. 障害復旧時の通信の流れ¶
FW01で発生したインスタンス障害が復旧した場合、Server-01、02はFW01、03を通してインターネットゲートウェイへ通信します。
注釈
FW03がDPDで復旧を検知して切り替え完了するまでに1分程度の時間がかかります。
インスタンス障害の試験方法として、FW01のインターフェイスを一時的に無効化する手法を採用しています。
任意のインターフェイスを無効化/有効化するコマンドは以下のとおりです。
無効化
# set interfaces [INTERFACE NAME] disable
有効化
# delete interfaces [INTERFACE NAME] disable
例
インターフェイス無効化の設定コマンド
# set interfaces ge-0/0/1.0 disable
# set interfaces ge-0/0/2.0 disable
インターフェイス有効化の設定コマンド
# delete interfaces ge-0/0/1.0 disable
# delete interfaces ge-0/0/2.0 disable
障害復旧時の状態確認
障害復旧時のFWの状態は以下のように確認できます。
VRRPの状態
FW01がMasterであることを確認できます。
user@FW01> show vrrp
Interface State Group VR state VR Mode Timer Type Address
ge-0/0/2.0 up 100 master Active A 1.083 lcl 192.168.1.101
vip 192.168.1.100
注釈
インターフェイスの有効化によりMasterを切り替えます。
FW02がBackupであることを確認できます。
user@FW02> show vrrp
Interface State Group VR state VR Mode Timer Type Address
ge-0/0/2.0 up 100 backup Active D 45.759lcl 192.168.1.102
vip 192.168.1.100
mas 192.168.1.101
FW03がMasterであることを確認できます。
user@FW03> show vrrp
Interface State Group VR state VR Mode Timer Type Address
ge-0/0/3.0 up 210 master Active A 11.441lcl 192.168.2.111
vip 192.168.2.110
FW04がBackupであることを確認できます。
user@FW04> show vrrp
Interface State Group VR state VR Mode Timer Type Address
ge-0/0/3.0 up 210 backup Active D 55.719lcl 192.168.2.112
vip 192.168.2.110
mas 192.168.2.111
トンネルの状態
FW01とFW03がIPsecトンネルを確立していることを確認できます。
user@FW01> show security ipsec sa
Total active tunnels: 1
ID Algorithm SPI Life:sec/kb Mon lsys Port Gateway
<131073 ESP:aes-gcm-256/None 367edd00 3525/ unlim - root 500 203.0.113.3
>131073 ESP:aes-gcm-256/None 965d2614 3525/ unlim - root 500 203.0.113.3
user@FW01> show security ike security-associations
Index State Initiator cookie Responder cookie Mode Remote Address
1843588 UP 002ac910851a14fb 5474a8e060a6de80 IKEv2 203.0.113.3
user@FW03> show security ipsec sa
Total active tunnels: 1 Total Ipsec sas: 1
ID Algorithm SPI Life:sec/kb Mon lsys Port Gateway
<131073 ESP:aes-gcm-256/None 965d2614 3499/ unlim - root 500 203.0.113.1
>131073 ESP:aes-gcm-256/None 367edd00 3499/ unlim - root 500 203.0.113.1
user@FW03> show security ike security-associations
Index State Initiator cookie Responder cookie Mode Remote Address
680514 UP 002ac910851a14fb 5474a8e060a6de80 IKEv2 203.0.113.1
FW02とFW04がVPNを確立していることを確認できます。
user@FW02> show security ipsec sa
Total active tunnels: 1
ID Algorithm SPI Life:sec/kb Mon lsys Port Gateway
<131073 ESP:aes-gcm-256/None 13dd35b6 2894/ unlim - root 500 203.0.113.4
>131073 ESP:aes-gcm-256/None e3626a29 2894/ unlim - root 500 203.0.113.4
user@FW02> show security ike security-associations
Index State Initiator cookie Responder cookie Mode Remote Address
65311 UP d083d530b49c9184 f5f370e8d5323a95 IKEv2 203.0.113.4
user@FW04> show security ipsec sa
Total active tunnels: 1 Total Ipsec sas: 1
ID Algorithm SPI Life:sec/kb Mon lsys Port Gateway
<131073 ESP:aes-gcm-256/None e3626a29 2911/ unlim - root 500 203.0.113.2
>131073 ESP:aes-gcm-256/None 13dd35b6 2911/ unlim - root 500 203.0.113.2
user@FW04> show security ike security-associations
Index State Initiator cookie Responder cookie Mode Remote Address
65395 UP a8f83271c302524c 80fefc81bb10c935 IKEv2 203.0.113.2
インターフェイスの状態
FW01のVPNトンネルインターフェイス(st)がUPしていることを確認できます。
user@FW01> show interfaces terse | no-more
Interface Admin Link Proto Local Remote
ge-0/0/1 up up
ge-0/0/1.0 up up inet 10.0.10.101/24
ge-0/0/2 up up
ge-0/0/2.0 up up inet 192.168.1.100/24
192.168.1.101/24
(中略)
lo0 up up
lo0.0 up up inet 203.0.113.1 --> 0/0
(中略)
st0 up up
st0.0 up down inet 10.1.1.101/24
user@FW01>
FW02のVPNトンネルインターフェイス(st)がUPしていることを確認できます。
user@FW02> show interfaces terse | no-more
Interface Admin Link Proto Local Remote
ge-0/0/1 up up
ge-0/0/1.0 up up inet 10.0.10.101/24
ge-0/0/2 up up
ge-0/0/2.0 up up inet 192.168.1.100/24
192.168.1.101/24
(中略)
lo0 up up
lo0.0 up up inet 203.0.113.2 --> 0/0
(中略)
st0 up up
st0.0 up up inet 10.1.1.101/24
user@FW02>
FW03のVPNトンネルインターフェイス(st)がupしていることを確認できます。
user@FW03> show interfaces terse | no-more
Interface Admin Link Proto Local Remote
ge-0/0/1 up up
ge-0/0/1.0 up up inet 10.0.20.111/24
ge-0/0/2 down down
ge-0/0/3 up up
ge-0/0/3.0 up up inet 192.168.2.110/24
192.168.2.111/24
(中略)
lo0 up up
lo0.0 up up inet 203.0.113.3 --> 0/0
(中略)
st0 up up
st0.0 up up inet 10.1.1.111/24
user@FW03>
FW04のVPNトンネルインターフェイス(st)がUPしていることを確認できます。
user@FW04> show interfaces terse | no-more
Interface Admin Link Proto Local Remote
ge-0/0/1 up up
ge-0/0/1.0 up up inet 10.0.20.112/24
ge-0/0/2 down down
ge-0/0/3 up up
ge-0/0/3.0 up up inet 192.168.2.112/24
(中略)
lo0 up up
lo0.0 up up inet 203.0.113.4 --> 0/0
(中略)
st0 up up
st0.0 up up inet 10.1.2.112/24
user@FW04>
ルーティングの状態
FW01の拠点A(192.168.2.0/24)に対する経路がVPNトンネルインターフェイス(st)に向いていることを確認できます。
user@FW01> show route | no-more
inet.0: 15 destinations, 15 routes (15 active, 0 holddown, 0 hidden)
+ = Active Route, - = Last Active, * = Both
0.0.0.0/0 *[Static/5] 00:01:54
> to 10.0.10.254 via ge-0/0/1.0
10.0.0.0/24 *[Direct/0] 1w0d 11:33:37
> via ge-0/0/0.0
10.0.0.101/32 *[Local/0] 1w0d 11:33:37
Local via ge-0/0/0.0
10.0.10.0/24 *[Direct/0] 00:01:54
> via ge-0/0/1.0
10.0.10.101/32 *[Local/0] 1w0d 11:33:37
Local via ge-0/0/1.0
10.1.1.0/24 *[Direct/0] 00:01:20
> via st0.0
10.1.1.101/32 *[Local/0] 1w0d 10:38:41
Local via st0.0
(中略)
192.168.1.0/24 *[Direct/0] 00:01:54
> via ge-0/0/2.0
192.168.1.100/32 *[Local/0] 00:00:19
Local via ge-0/0/2.0
192.168.1.101/32 *[Local/0] 1w0d 11:33:37
Local via ge-0/0/2.0
192.168.2.0/24 *[Static/5] 00:01:20
> via st0.0
user@FW01>
FW02の拠点A(192.168.2.0/24)に対する経路がVPNトンネルインターフェイス(st)に向いていることを確認できます。
user@FW02> show route | no-more
inet.0: 14 destinations, 14 routes (14 active, 0 holddown, 0 hidden)
+ = Active Route, - = Last Active, * = Both
0.0.0.0/0 *[Static/5] 1w0d 09:42:37
> to 10.0.10.254 via ge-0/0/1.0
10.0.0.0/24 *[Direct/0] 1w0d 11:31:53
> via ge-0/0/0.0
10.0.0.102/32 *[Local/0] 1w0d 11:31:53
Local via ge-0/0/0.0
10.0.10.0/24 *[Direct/0] 1w0d 11:31:53
> via ge-0/0/1.0
10.0.10.102/32 *[Local/0] 1w0d 11:31:53
Local via ge-0/0/1.0
10.1.2.0/24 *[Direct/0] 00:29:04
> via st0.0
10.1.2.102/32 *[Local/0] 1w0d 10:35:43
Local via st0.0
(中略)
192.168.1.0/24 *[Direct/0] 1w0d 09:12:42
> via ge-0/0/2.0
192.168.1.102/32 *[Local/0] 1w0d 11:31:53
Local via ge-0/0/2.0
192.168.2.0/24 *[Static/5] 00:29:04
> via st0.0
user@FW02>
FW03の拠点A(192.168.2.0/24)に対する経路がVPNトンネルインターフェイス(st)に向いていることを確認できます。
user@FW03> show route | no-more
inet.0: 15 destinations, 15 routes (15 active, 0 holddown, 0 hidden)
+ = Active Route, - = Last Active, * = Both
0.0.0.0/0 *[Static/5] 1w0d 10:04:43
> to 10.0.20.254 via ge-0/0/1.0
10.0.0.0/24 *[Direct/0] 1w0d 11:30:08
> via ge-0/0/0.0
10.0.0.111/32 *[Local/0] 1w0d 11:30:08
Local via ge-0/0/0.0
10.0.20.0/24 *[Direct/0] 1w0d 10:26:36
> via ge-0/0/1.0
10.0.20.111/32 *[Local/0] 1w0d 10:26:36
Local via ge-0/0/1.0
10.1.1.0/24 *[Direct/0] 00:01:24
> via st0.0
10.1.1.111/32 *[Local/0] 00:01:24
Local via st0.0
(中略)
192.168.1.0/24 *[Static/5] 00:01:24
> via st0.0
192.168.2.0/24 *[Direct/0] 1w0d 10:26:35
> via ge-0/0/3.0
192.168.2.110/32 *[Local/0] 00:01:19
Local via ge-0/0/3.0
192.168.2.111/32 *[Local/0] 1w0d 10:26:35
Local via ge-0/0/3.0
user@FW03>
FW04の拠点A(192.168.2.0/24)に対する経路がVPNトンネルインターフェイス(st)に向いていることを確認できます。
user@FW04> show route | no-more
inet.0: 14 destinations, 14 routes (14 active, 0 holddown, 0 hidden)
+ = Active Route, - = Last Active, * = Both
0.0.0.0/0 *[Static/5] 1w0d 09:43:02
> to 10.0.20.254 via ge-0/0/1.0
10.0.0.0/24 *[Direct/0] 1w0d 11:19:12
> via ge-0/0/0.0
10.0.0.112/32 *[Local/0] 1w0d 11:19:12
Local via ge-0/0/0.0
10.0.20.0/24 *[Direct/0] 1w0d 11:19:12
> via ge-0/0/1.0
10.0.20.112/32 *[Local/0] 1w0d 11:19:12
Local via ge-0/0/1.0
10.1.2.0/24 *[Direct/0] 1w0d 09:42:10
> via st0.0
10.1.2.112/32 *[Local/0] 1w0d 09:42:10
Local via st0.0
(中略)
192.168.1.0/24 *[Static/5] 1w0d 09:42:10
> via st0.0
192.168.2.0/24 *[Direct/0] 1w0d 11:19:12
> via ge-0/0/3.0
192.168.2.112/32 *[Local/0] 1w0d 11:19:12
Local via ge-0/0/3.0
user@FW04>
サーバーの接続確認
ping、HTTP通信が正常(OK)であることを確認します。
Server-01
pingコマンドを用いて通信を確認します。
[root@Server-01 ~]# ping -c 5 192.168.2.12
PING 192.168.2.12 (192.168.2.12) 56(84) bytes of data.
64 bytes from 192.168.2.12: icmp_seq=1 ttl=62 time=7.02 ms
64 bytes from 192.168.2.12: icmp_seq=2 ttl=62 time=1.45 ms
64 bytes from 192.168.2.12: icmp_seq=3 ttl=62 time=1.34 ms
64 bytes from 192.168.2.12: icmp_seq=4 ttl=62 time=3.01 ms
64 bytes from 192.168.2.12: icmp_seq=5 ttl=62 time=1.93 ms
--- 192.168.2.12 ping statistics ---
5 packets transmitted, 5 received, 0% packet loss, time 4005ms
rtt min/avg/max/mdev = 1.346/2.953/7.024/2.119 ms
[root@Server-01 ~]#
Server-02
pingコマンドを用いて通信を確認します。
[root@Server-02 ~]# ping -c 5 192.168.1.11
PING 192.168.1.11 (192.168.1.11) 56(84) bytes of data.
64 bytes from 192.168.1.11: icmp_seq=1 ttl=62 time=4.81 ms
64 bytes from 192.168.1.11: icmp_seq=2 ttl=62 time=1.66 ms
64 bytes from 192.168.1.11: icmp_seq=3 ttl=62 time=1.56 ms
64 bytes from 192.168.1.11: icmp_seq=4 ttl=62 time=1.56 ms
64 bytes from 192.168.1.11: icmp_seq=5 ttl=62 time=1.52 ms
--- 192.168.1.11 ping statistics ---
5 packets transmitted, 5 received, 0% packet loss, time 4007ms
rtt min/avg/max/mdev = 1.528/2.226/4.815/1.296 ms
[root@Server-02 ~]#
curlコマンドを用いてHTTP通信を確認します。
[root@server-02 ~]# curl -i http://192.168.1.11
HTTP/1.1 200 OK
Date: Tue, 03 Mar 2020 12:03:08 GMT
Server: Apache/2.4.6 (CentOS)
Last-Modified: Fri, 07 Feb 2020 05:46:48 GMT
ETag: "7d-59df5ea63a394"
Accept-Ranges: bytes
Content-Length: 125
Content-Type: text/html; charset=UTF-8
<html>
<head><title>Server01</title></head>
<body>
<p>Web Server01 test page</p>
</body>
</html>