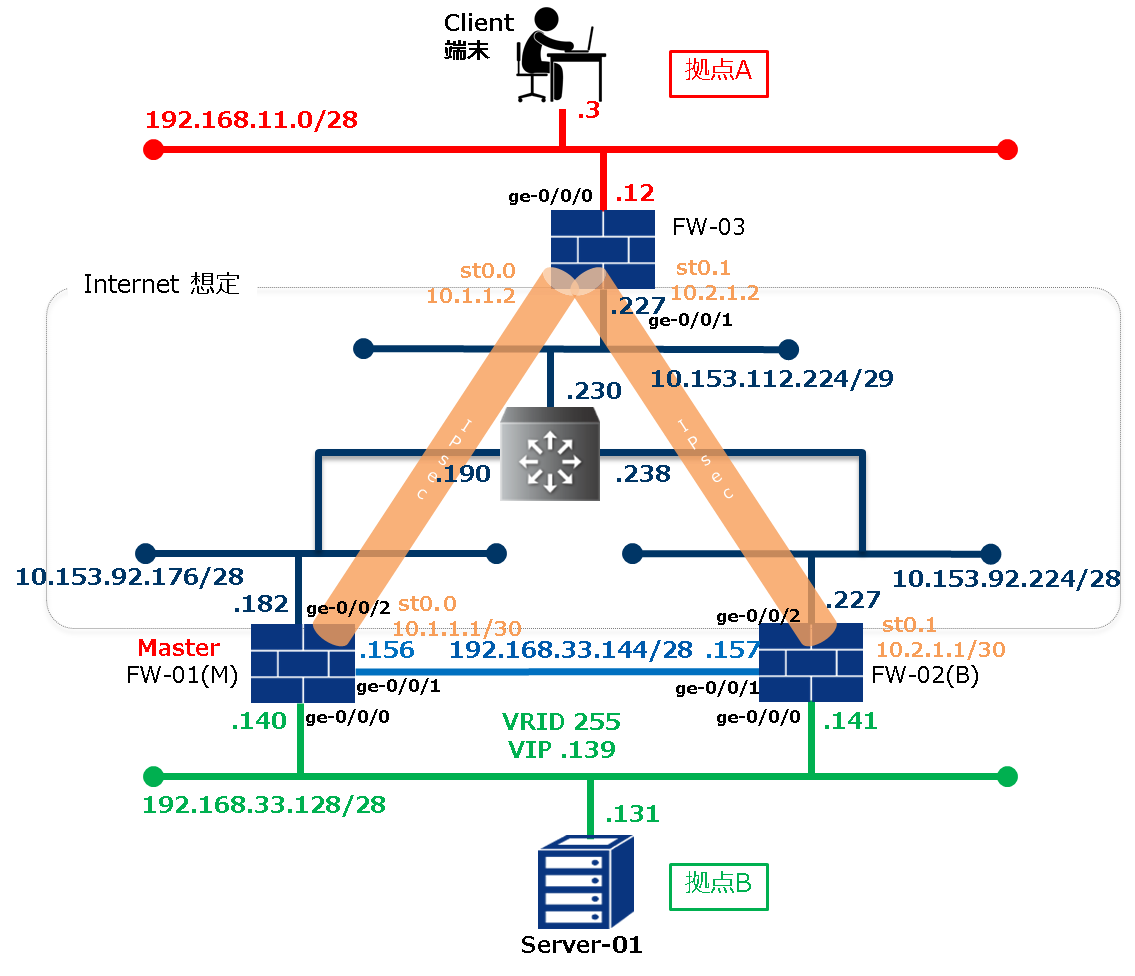
1.3. サイト間VPN構成例¶
本構成はVPNトンネルインターフェイス(st)を利用したサイト間IPsec-VPNを構築しています。
システム構成図のとおり複数のIPsecトンネルを構築し、stに向けたスタティックルートを切り替えるフローティングスタティックを使用することにより冗長構成を実現しています。
IPsecの接続先にVRRPのVirtual IPアドレス(以下VIP)を設定することができないため、冗長構成を実現するには本構成例を推奨します。
注釈
フローティングスタティック
1つの宛先ネットワーク(以下NW)へ到達するために複数の通信経路(ネクストホップ)を優先度をつけた形で設定しておき、優先度の高い経路が使用できなくなった際、経路情報として優先度の低い通信経路が自動的に採用される仕組みです。
1.3.1. システム構成図¶
1.3.2. ファイアウォール設定の内容¶
ファイアウォールフェイス設定
構成図のとおりにIPアドレスの設定を実施します。
FW-01
# set interfaces ge-0/0/0 unit 0 family inet address 192.168.33.140/28
# set interfaces ge-0/0/1 unit 0 family inet address 192.168.33.156/28
# set interfaces ge-0/0/2 unit 0 family inet address 10.153.92.182/28
# set interfaces st0 unit 0 family inet address 10.1.1.1/30
FW-02
# set interfaces ge-0/0/0 unit 0 family inet address 192.168.33.141/28
# set interfaces ge-0/0/1 unit 0 family inet address 192.168.33.157/28
# set interfaces ge-0/0/2 unit 0 family inet address 10.153.92.227/28
# set interfaces st0 unit 1 family inet address 10.2.1.1/30
FW-03
# set interfaces ge-0/0/0 unit 0 family inet address 192.168.11.12/28
# set interfaces ge-0/0/1 unit 0 family inet address 10.153.112.227/29
# set interfaces st0 unit 0 family inet address 10.1.1.2/30
# set interfaces st0 unit 1 family inet address 10.2.1.2/30
注釈
vSRXへのインターフェイス(ge)へのIPアドレス設定前にSmart Data Platformポータル(以下SDPFポータル)画面で利用インターフェイスとIPアドレスを設定します。
インターフェイスのゾーン設定
FW-01のゾーン設定
# set security zones security-zone trust interfaces ge-0/0/0.0
# set security zones security-zone trust interfaces ge-0/0/1.0
# set security zones security-zone untrust host-inbound-traffic system-services ike
# set security zones security-zone untrust interfaces ge-0/0/2.0
# set security zones security-zone untrust interfaces st0.0
FW-02のゾーン設定
# set security zones security-zone trust interfaces ge-0/0/0.0
# set security zones security-zone trust interfaces ge-0/0/1.0
# set security zones security-zone untrust host-inbound-traffic system-services ike
# set security zones security-zone untrust interfaces ge-0/0/2.0
# set security zones security-zone untrust interfaces st0.1
FW-03のゾーン設定
# set security zones security-zone trust interfaces ge-0/0/0.0
# set security zones security-zone untrust host-inbound-traffic system-services ike
# set security zones security-zone untrust interfaces ge-0/0/1.0
# set security zones security-zone untrust interfaces st0.0
# set security zones security-zone untrust interfaces st0.1
ゾーンベースファイアウォールのポリシー設定
FW-01 ならびに FW-02 のゾーン間のポリシー設定
# set security address-book global address CLIENT_LAN 192.168.11.0/28
# set security policies from-zone trust to-zone trust policy default-permit match source-address any
# set security policies from-zone trust to-zone trust policy default-permit match destination-address any
# set security policies from-zone trust to-zone trust policy default-permit match application any
# set security policies from-zone trust to-zone trust policy default-permit then permit
# set security policies from-zone trust to-zone untrust policy default-permit match source-address any
# set security policies from-zone trust to-zone untrust policy default-permit match destination-address any
# set security policies from-zone trust to-zone untrust policy default-permit match application any
# set security policies from-zone trust to-zone untrust policy default-permit then permit
# set security policies from-zone untrust to-zone trust policy CLIENT_LAN_PERMIT match source-address CLIENT_LAN
# set security policies from-zone untrust to-zone trust policy CLIENT_LAN_PERMIT match destination-address any
# set security policies from-zone untrust to-zone trust policy CLIENT_LAN_PERMIT match application any
# set security policies from-zone untrust to-zone trust policy CLIENT_LAN_PERMIT then permit
# set security policies from-zone untrust to-zone trust policy ALL-DENY match source-address any
# set security policies from-zone untrust to-zone trust policy ALL-DENY match destination-address any
# set security policies from-zone untrust to-zone trust policy ALL-DENY match application any
# set security policies from-zone untrust to-zone trust policy ALL-DENY then deny
FW-03のゾーン間のポリシー設定
# set security address-book global address SERVER01_LAN 192.168.33.128/28
# set security policies from-zone trust to-zone trust policy default-permit match source-address any
# set security policies from-zone trust to-zone trust policy default-permit match destination-address any
# set security policies from-zone trust to-zone trust policy default-permit match application any
# set security policies from-zone trust to-zone trust policy default-permit then permit
# set security policies from-zone trust to-zone untrust policy default-permit match source-address any
# set security policies from-zone trust to-zone untrust policy default-permit match destination-address any
# set security policies from-zone trust to-zone untrust policy default-permit match application any
# set security policies from-zone trust to-zone untrust policy default-permit then permit
# set security policies from-zone untrust to-zone trust policy SERVER01_LAN_PERMIT match source-address SERVER01_LAN
# set security policies from-zone untrust to-zone trust policy SERVER01_LAN_PERMIT match destination-address any
# set security policies from-zone untrust to-zone trust policy SERVER01_LAN_PERMIT match application any
# set security policies from-zone untrust to-zone trust policy SERVER01_LAN_PERMIT then permit
# set security policies from-zone untrust to-zone trust policy ALL-DENY match source-address any
# set security policies from-zone untrust to-zone trust policy ALL-DENY match destination-address any
# set security policies from-zone untrust to-zone trust policy ALL-DENY match application any
# set security policies from-zone untrust to-zone trust policy ALL-DENY then deny
VRRP設定
正常時にFW-01がMasterとなる設定をします。
FW-01
# set security zones security-zone trust host-inbound-traffic protocols all
# set interfaces ge-0/0/0 unit 0 family inet address 192.168.33.140/28 vrrp-group 255 virtual-address 192.168.33.139
# set interfaces ge-0/0/0 unit 0 family inet address 192.168.33.140/28 vrrp-group 255 priority 110
# set interfaces ge-0/0/0 unit 0 family inet address 192.168.33.140/28 vrrp-group 255 preempt
# set interfaces ge-0/0/0 unit 0 family inet address 192.168.33.140/28 vrrp-group 255 accept-data
# set interfaces ge-0/0/0 unit 0 family inet address 192.168.33.140/28 vrrp-group 255 advertise-interval 5
FW-02
# set security zones security-zone trust host-inbound-traffic protocols all
# set interfaces ge-0/0/0 unit 0 family inet address 192.168.33.141/28 vrrp-group 255 virtual-address 192.168.33.139
# set interfaces ge-0/0/0 unit 0 family inet address 192.168.33.141/28 vrrp-group 255 priority 90
# set interfaces ge-0/0/0 unit 0 family inet address 192.168.33.141/28 vrrp-group 255 preempt
# set interfaces ge-0/0/0 unit 0 family inet address 192.168.33.141/28 vrrp-group 255 accept-data
# set interfaces ge-0/0/0 unit 0 family inet address 192.168.33.141/28 vrrp-group 255 advertise-interval 5
注釈
VRRP設定前に、必ずSDPFポータル上で「許可されたアドレスペアの編集」を実施してください。
FW-03はシングル構成のため、VRRP設定はありません。
VPN設定(IPsec)
IPsecを設定する際に利用したパラメータについて以下に示します。
パラメータ |
値 |
|---|---|
Phase1 |
|
Authentication Method |
Pre-shared key |
Pre-shared key password |
IPSEC_KEY_1 |
DH group |
group14 |
Encryption Algorithm |
AES256-GCM |
ISAKMP SA lifetime |
28800 seconds |
IKE version |
v2only |
Phase2 |
|
Security protocol |
ESP |
Encryption Algorithm |
AES256-GCM |
IPSEC SA lifetime |
3600 seconds |
perfect-forward-secrecy keys |
group14 |
Establish-tunnel |
immediately |
FW-01,02,03 共通設定
IKEフェーズ1設定
# set security ike proposal IKE_PROP1 authentication-method pre-shared-keys
# set security ike proposal IKE_PROP1 dh-group group14
# set security ike proposal IKE_PROP1 encryption-algorithm aes-256-gcm
# set security ike proposal IKE_PROP1 lifetime-seconds 28800
# set security ike policy IKE_POL1 mode main
# set security ike policy IKE_POL1 proposals IKE_PROP1
# set security ike policy IKE_POL1 pre-shared-key ascii-text IPSEC_KEY_1
IKEフェーズ2設定
# set security ipsec proposal IPSEC_PROP1 protocol esp
# set security ipsec proposal IPSEC_PROP1 encryption-algorithm aes-256-gcm
# set security ipsec proposal IPSEC_PROP1 lifetime-seconds 3600
# set security ipsec policy IPSEC_POL1 perfect-forward-secrecy keys group14
# set security ipsec policy IPSEC_POL1 proposals IPSEC_PROP1
FW-01 サイト間接続の設定
# set security ike gateway GW1 ike-policy IKE_POL1
# set security ike gateway GW1 address 10.153.112.227
# set security ike gateway GW1 external-interface ge-0/0/2.0
# set security ike gateway GW1 version v2-only
# set security ike gateway GW1 dead-peer-detection optimized
# set security ike gateway GW1 dead-peer-detection interval 10
# set security ike gateway GW1 dead-peer-detection threshold 5
# set security ipsec vpn VPN1 bind-interface st0.0
# set security ipsec vpn VPN1 ike gateway GW1
# set security ipsec vpn VPN1 ike ipsec-policy IPSEC_POL1
# set security ipsec vpn VPN1 establish-tunnels immediately
FW-02 サイト間接続の設定
# set security ike gateway GW1 ike-policy IKE_POL1
# set security ike gateway GW1 address 10.153.112.227
# set security ike gateway GW1 external-interface ge-0/0/2.0
# set security ike gateway GW1 version v2-only
# set security ike gateway GW1 dead-peer-detection optimized
# set security ike gateway GW1 dead-peer-detection interval 10
# set security ike gateway GW1 dead-peer-detection threshold 5
# set security ipsec vpn VPN1 bind-interface st0.1
# set security ipsec vpn VPN1 ike gateway GW1
# set security ipsec vpn VPN1 ike ipsec-policy IPSEC_POL1
# set security ipsec vpn VPN1 establish-tunnels immediately
FW-03 サイト間接続の設定
# set security ike gateway GW1 ike-policy IKE_POL1
# set security ike gateway GW1 address 10.153.92.182
# set security ike gateway GW1 dead-peer-detection optimized
# set security ike gateway GW1 dead-peer-detection interval 10
# set security ike gateway GW1 dead-peer-detection threshold 5
# set security ike gateway GW1 external-interface ge-0/0/1.0
# set security ike gateway GW1 version v2-only
# set security ike gateway GW2 ike-policy IKE_POL1
# set security ike gateway GW2 address 10.153.92.227
# set security ike gateway GW2 dead-peer-detection optimized
# set security ike gateway GW2 dead-peer-detection interval 10
# set security ike gateway GW2 dead-peer-detection threshold 5
# set security ike gateway GW2 external-interface ge-0/0/1.0
# set security ike gateway GW2 version v2-only
# set security ipsec vpn VPN1 bind-interface st0.0
# set security ipsec vpn VPN1 ike gateway GW1
# set security ipsec vpn VPN1 ike ipsec-policy IPSEC_POL1
# set security ipsec vpn VPN1 establish-tunnels immediately
# set security ipsec vpn VPN2 bind-interface st0.1
# set security ipsec vpn VPN2 ike gateway GW2
# set security ipsec vpn VPN2 ike ipsec-policy IPSEC_POL1
# set security ipsec vpn VPN2 establish-tunnels immediately
注釈
各ファイアウォール(以下FW)では、IPsec対向装置間で通信障害が発生した場合に異常を検知し、通信経路を切り替えるためのDead Peer Detection(以下DPD)の設定をしています。 DPDのモードである「optimized」はIPsecトンネルを最後に通過した通信から戻りの通信が無い場合に、DPDによる監視をスタートします。 製品の仕様上、監視のパラメータはインターバルが10秒、閾値が5回となっており、回線断の検知と切り替わり完了まで1分程度の時間がかかります。
ルーティング設定
FW-01
# set routing-options static route 0.0.0.0/0 next-hop 10.153.92.190
# set routing-options static route 192.168.11.0/28 next-hop st0.0
FW-02
# set routing-options static route 0.0.0.0/0 next-hop 10.153.92.238
# set routing-options static route 192.168.11.0/28 next-hop st0.1
FW-03
# set routing-options static route 0.0.0.0/0 next-hop 10.153.112.230
# set routing-options static route 192.168.33.128/28 next-hop st0.0
# set routing-options static route 192.168.33.128/28 qualified-next-hop st0.1 preference 7
設定内容の確認
前述の設定が正しく投入されている場合、以下の出力を確認できます。
FW-01 コンフィグレーション
user01@FW-01> show configuration
(中略)
security {
ike {
proposal IKE_PROP1 {
authentication-method pre-shared-keys;
dh-group group14;
encryption-algorithm aes-256-gcm;
lifetime-seconds 28800;
}
policy IKE_POL1 {
mode main;
proposals IKE_PROP1;
pre-shared-key ascii-text "$9$mPF/u0Icrv1RZDkmF3Ap0BSes2oJUj"; ## SECRET-DATA
}
gateway GW1 {
ike-policy IPSEC_POL1;
address 10.153.112.227;
dead-peer-detection {
optimized;
interval 10;
threshold 5;
}
external-interface ge-0/0/2.0;
version v2-only;
}
}
ipsec {
proposal IPSEC_PROP1 {
protocol esp;
encryption-algorithm aes-256-gcm;
lifetime-seconds 3600;
}
policy IPSEC_POL1 {
perfect-forward-secrecy {
keys group14;
}
proposals IPSEC_PROP1;
}
vpn VPN1 {
bind-interface st0.0;
ike {
gateway GW1;
ipsec-policy IPSEC_POL1;
}
establish-tunnels immediately;
}
}
address-book {
global {
address CLIENT_LAN 192.168.11.0/28;
}
}
policies {
from-zone trust to-zone trust {
policy default-permit {
match {
source-address any;
destination-address any;
application any;
}
then {
permit;
}
}
}
from-zone trust to-zone untrust {
policy default-permit {
match {
source-address any;
destination-address any;
application any;
}
then {
permit;
}
}
}
from-zone untrust to-zone trust {
policy CLIENT_LAN_PERMIT {
match {
source-address CLIENT_LAN;
destination-address any;
application any;
}
then {
permit;
}
}
policy ALL-DENY {
match {
source-address any;
destination-address any;
application any;
}
then {
deny;
}
}
}
}
zones {
security-zone trust {
host-inbound-traffic {
system-services {
all;
}
protocols {
all;
}
}
interfaces {
ge-0/0/0.0;
ge-0/0/1.0;
}
}
security-zone untrust {
host-inbound-traffic {
system-services {
ping;
ike;
}
}
interfaces {
ge-0/0/2.0;
st0.0;
}
}
}
}
interfaces {
ge-0/0/0 {
unit 0 {
family inet {
address 192.168.33.140/28 {
vrrp-group 255 {
virtual-address 192.168.33.139;
priority 110;
advertise-interval 5;
preempt;
accept-data;
}
}
}
}
}
ge-0/0/1 {
unit 0 {
family inet {
address 192.168.33.156/28;
}
}
}
ge-0/0/2 {
unit 0 {
family inet {
address 10.153.92.182/28;
}
}
}
st0 {
unit 0 {
family inet {
address 10.1.1.1/30;
}
}
}
}
routing-options {
static {
route 0.0.0.0/0 next-hop 10.153.92.190;
route 192.168.11.0/28 next-hop st0.0;
}
}
FW-02 コンフィグレーション
user01@FW-02> show configuration
(中略)
security {
ike {
proposal IKE_PROP1 {
authentication-method pre-shared-keys;
dh-group group14;
encryption-algorithm aes-256-gcm;
lifetime-seconds 28800;
}
policy IKE_POL1 {
mode main;
proposals IKE_PROP1;
pre-shared-key ascii-text "$9$3P9TntOhclMLNreqPQ3tpIEcyWxZUikmf"; ## SECRET-DATA
}
gateway GW1 {
ike-policy IKE_POL1;
address 10.153.112.227;
dead-peer-detection {
optimized;
interval 10;
threshold 5;
}
external-interface ge-0/0/2.0;
version v2-only;
}
}
ipsec {
proposal IPSEC_PROP1 {
protocol esp;
encryption-algorithm aes-256-gcm;
lifetime-seconds 3600;
}
policy IPSEC_POL1 {
perfect-forward-secrecy {
keys group14;
}
proposals IPSEC_PROP1;
}
vpn VPN1 {
bind-interface st0.1;
ike {
gateway GW1;
ipsec-policy IPSEC_POL1;
}
establish-tunnels immediately;
}
}
address-book {
global {
address CLIENT_LAN 192.168.11.0/28;
}
}
policies {
from-zone trust to-zone trust {
policy default-permit {
match {
source-address any;
destination-address any;
application any;
}
then {
permit;
}
}
}
from-zone trust to-zone untrust {
policy default-permit {
match {
source-address any;
destination-address any;
application any;
}
then {
permit;
}
}
}
from-zone untrust to-zone trust {
policy CLIENT_LAN_PERMIT {
match {
source-address CLIENT_LAN;
destination-address any;
application any;
}
then {
permit;
}
}
policy ALL-DENY {
match {
source-address any;
destination-address any;
application any;
}
then {
deny;
}
}
}
}
zones {
security-zone trust {
host-inbound-traffic {
system-services {
all;
}
protocols {
all;
}
}
interfaces {
ge-0/0/0.0;
ge-0/0/1.0;
}
}
security-zone untrust {
host-inbound-traffic {
system-services {
ping;
ike;
}
}
interfaces {
ge-0/0/2.0;
st0.1;
}
}
}
}
interfaces {
ge-0/0/0 {
unit 0 {
family inet {
address 192.168.33.141/28 {
vrrp-group 255 {
virtual-address 192.168.33.139;
priority 90;
advertise-interval 5;
preempt;
accept-data;
}
}
}
}
}
ge-0/0/1 {
unit 0 {
family inet {
address 192.168.33.157/28;
}
}
}
ge-0/0/2 {
unit 0 {
family inet {
address 10.153.92.227/28;
}
}
}
st0 {
unit 1 {
family inet {
address 10.2.1.1/30;
}
}
}
}
routing-options {
static {
route 0.0.0.0/0 next-hop 10.153.92.238;
route 192.168.11.0/28 next-hop st0.1;
}
}
FW-03 コンフィグレーション
user01@FW-03> show configuration
(中略)
security {
ike {
proposal IKE_PROP1 {
authentication-method pre-shared-keys;
dh-group group14;
encryption-algorithm aes-256-gcm;
lifetime-seconds 28800;
}
policy IKE_POL1 {
mode main;
proposals IKE_PROP1;
pre-shared-key ascii-text "$9$EQhheWN-wgaUbsAu1EeKX7-V4Zz3/Cp0"; ## SECRET-DATA
}
gateway GW1 {
ike-policy IKE_POL1;
address 10.153.92.182;
dead-peer-detection {
optimized;
interval 10;
threshold 5;
}
external-interface ge-0/0/1.0;
version v2-only;
}
gateway GW2 {
ike-policy IKE_POL1;
address 10.153.92.227;
dead-peer-detection {
optimized;
interval 10;
threshold 5;
}
external-interface ge-0/0/1.0;
version v2-only;
}
}
ipsec {
proposal IPSEC_PROP1 {
protocol esp;
encryption-algorithm aes-256-gcm;
lifetime-seconds 3600;
}
policy IPSEC_POL1 {
perfect-forward-secrecy {
keys group14;
}
proposals IPSEC_PROP1;
}
vpn VPN1 {
bind-interface st0.0;
ike {
gateway GW1;
ipsec-policy IPSEC_POL1;
}
establish-tunnels immediately;
}
vpn VPN2 {
bind-interface st0.1;
ike {
gateway GW2;
ipsec-policy IPSEC_POL1;
}
establish-tunnels immediately;
}
}
address-book {
global {
address SERVER01_LAN 192.168.33.128/28;
}
}
policies {
from-zone trust to-zone trust {
policy default-permit {
match {
source-address any;
destination-address any;
application any;
}
then {
permit;
}
}
}
from-zone trust to-zone untrust {
policy default-permit {
match {
source-address any;
destination-address any;
application any;
}
then {
permit;
}
}
}
from-zone untrust to-zone trust {
policy SERVER01_LAN_PERMIT {
match {
source-address SERVER01_LAN;
destination-address any;
application any;
}
then {
permit;
}
}
policy ALL-DENY {
match {
source-address any;
destination-address any;
application any;
}
then {
deny;
}
}
}
}
zones {
security-zone trust {
host-inbound-traffic {
system-services {
all;
}
protocols {
all;
}
}
interfaces {
ge-0/0/0.0;
}
}
security-zone untrust {
host-inbound-traffic {
system-services {
ping;
ike;
}
}
interfaces {
ge-0/0/1.0;
st0.0;
st0.1;
}
}
}
}
interfaces {
ge-0/0/0 {
unit 0 {
family inet {
address 192.168.11.12/28;
}
}
}
ge-0/0/1 {
unit 0 {
family inet {
address 10.153.112.227/29;
}
}
}
st0 {
unit 0 {
family inet {
address 10.1.1.2/30;
}
}
unit 1 {
family inet {
address 10.2.1.2/30;
}
}
}
}
routing-options {
static {
route 0.0.0.0/0 next-hop 10.153.112.230;
route 192.168.33.128/28 {
next-hop st0.0;
qualified-next-hop st0.1 {
preference 7;
}
}
}
}
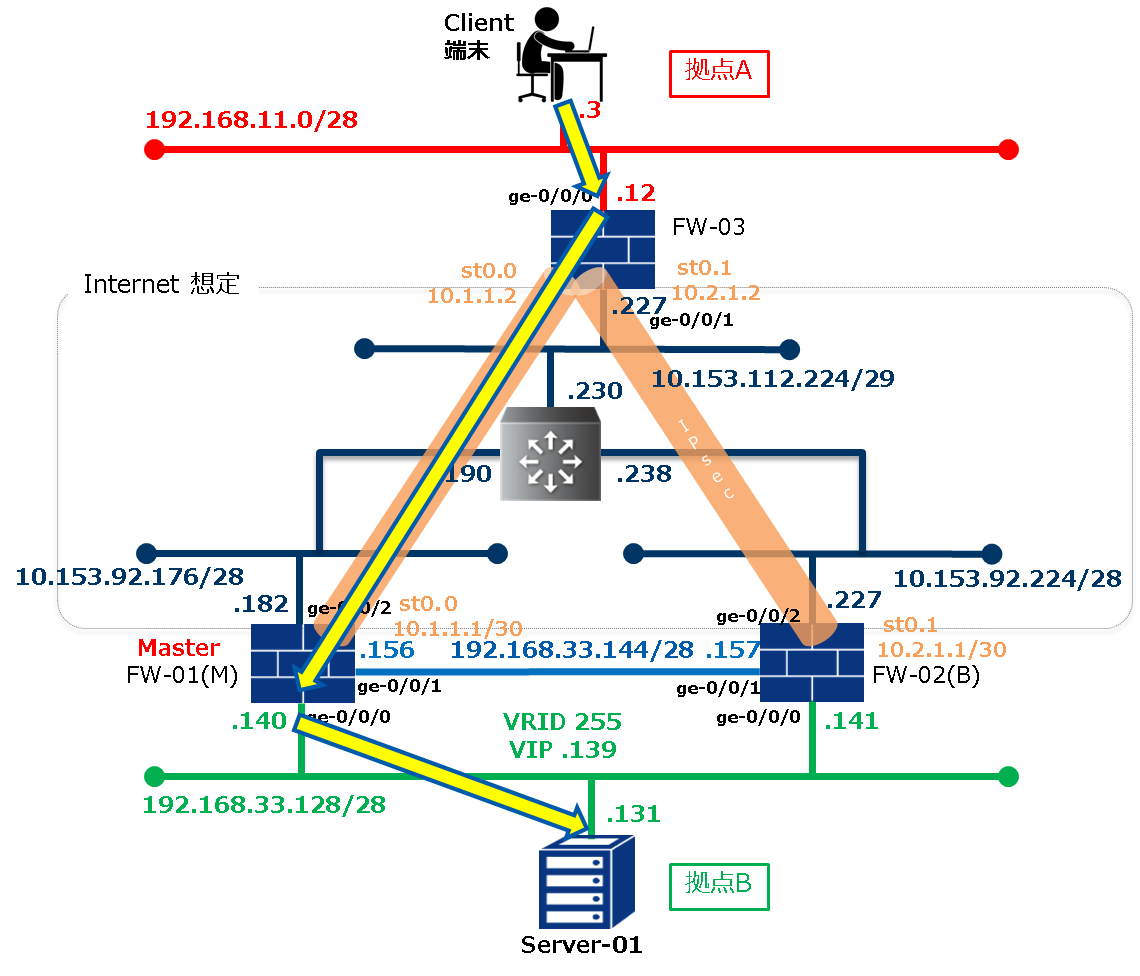
1.3.3. 通信の流れ¶
正常時の状態確認
正常通信時のFWの状態は以下のように確認できます。
VRRPの状態
FW-01がMasterであること。
user01@FW-01> show vrrp
Interface State Group VR state VR Mode Timer Type Address
ge-0/0/0.0 up 255 master Active A 0.914 lcl 192.168.33.140
vip 192.168.33.139
FW-02がBackupであること。
user01@FW-02> show vrrp
Interface State Group VR state VR Mode Timer Type Address
ge-0/0/0.0 up 255 backup Active D 2.913 lcl 192.168.33.141
vip 192.168.33.139
mas 192.168.33.140
VPNの状態
FW-01とFW-03がIPsecトンネルを確立できていること。
user01@FW-01> show security ike security-associations
Index State Initiator cookie Responder cookie Mode Remote Address
5507280 UP bf4cab74984df1be 76646dd99aa54cc3 IKEv2 10.153.112.227
user01@FW-01> show security ipsec security-associations
Total active tunnels: 1
ID Algorithm SPI Life:sec/kb Mon lsys Port Gateway
<131073 ESP:aes-gcm-256/None 286ed4d2 3021/ unlim - root 500 10.153.112.227
>131073 ESP:aes-gcm-256/None 361250c8 3021/ unlim - root 500 10.153.112.227
FW-02とFW-03がIPsecトンネルを確立できていること。
user01@FW-02> show security ike security-associations
Index State Initiator cookie Responder cookie Mode Remote Address
5424791 UP 5139fb1f4157c45f d4cc3956285be395 IKEv2 10.153.112.227
user01@FW-02> show security ipsec security-associations
Total active tunnels: 1
ID Algorithm SPI Life:sec/kb Mon lsys Port Gateway
<131073 ESP:aes-gcm-256/None 6032218a 1759/ unlim - root 500 10.153.112.227
>131073 ESP:aes-gcm-256/None a4342f08 1759/ unlim - root 500 10.153.112.227
FW-03とFW-01,02がIPsecトンネルを確立できていること。
user01@FW-03> show security ike security-associations
Index State Initiator cookie Responder cookie Mode Remote Address
6898200 UP 5139fb1f4157c45f d4cc3956285be395 IKEv2 10.153.92.227
6898208 UP bf4cab74984df1be 76646dd99aa54cc3 IKEv2 10.153.92.182
user01@FW-03> show security ipsec security-associations
Total active tunnels: 2
ID Algorithm SPI Life:sec/kb Mon lsys Port Gateway
<131073 ESP:aes-gcm-256/None 361250c8 2843/ unlim - root 500 10.153.92.182
>131073 ESP:aes-gcm-256/None 286ed4d2 2843/ unlim - root 500 10.153.92.182
<131074 ESP:aes-gcm-256/None a4342f08 1582/ unlim - root 500 10.153.92.227
>131074 ESP:aes-gcm-256/None 6032218a 1582/ unlim - root 500 10.153.92.227
インターフェイスの状態
FW-01のst0.0がUPしていること。
user01@FW-01> show interfaces terse | no-more
Interface Admin Link Proto Local Remote
ge-0/0/0 up up
ge-0/0/0.0 up up inet 192.168.33.139/28
192.168.33.140/28
gr-0/0/0 up up
ip-0/0/0 up up
lsq-0/0/0 up up
lt-0/0/0 up up
mt-0/0/0 up up
sp-0/0/0 up up
sp-0/0/0.0 up up inet
inet6
sp-0/0/0.16383 up up inet
ge-0/0/1 up up
ge-0/0/1.0 up up inet 192.168.33.156/28
ge-0/0/2 up up
ge-0/0/2.0 up up inet 10.153.92.182/28
(中略)
st0 up up
st0.0 up up inet 10.1.1.1/30
tap up up
vlan up down
vtep up up
user01@FW-01>
FW-02のst0.1がUPしていること。
user01@FW-02> show interfaces terse | no-more
Interface Admin Link Proto Local Remote
ge-0/0/0 up up
ge-0/0/0.0 up up inet 192.168.33.141/28
gr-0/0/0 up up
ip-0/0/0 up up
lsq-0/0/0 up up
lt-0/0/0 up up
mt-0/0/0 up up
sp-0/0/0 up up
sp-0/0/0.0 up up inet
inet6
sp-0/0/0.16383 up up inet
ge-0/0/1 up up
ge-0/0/1.0 up up inet 192.168.33.157/28
ge-0/0/2 up up
ge-0/0/2.0 up up inet 10.153.92.227/28
(中略)
st0 up up
st0.1 up up inet 10.2.1.1/30
tap up up
vlan up down
vtep up up
user01@FW-02>
FW-03のst0.0,st0.1がUPしていること。
user01@FW-03> show interfaces terse | no-more
Interface Admin Link Proto Local Remote
ge-0/0/0 up up
ge-0/0/0.0 up up inet 192.168.11.12/28
gr-0/0/0 up up
ip-0/0/0 up up
lsq-0/0/0 up up
lt-0/0/0 up up
mt-0/0/0 up up
sp-0/0/0 up up
sp-0/0/0.0 up up inet
inet6
sp-0/0/0.16383 up up inet
ge-0/0/1 up up
ge-0/0/1.0 up up inet 10.153.112.227/29
(中略)
st0 up up
st0.0 up up inet 10.1.1.2/30
st0.1 up up inet 10.2.1.2/30
tap up up
vlan up down
vtep up up
user01@FW-03>
ルーティングの状態
FW-01の拠点A192.168.11.0/28)に対するルートがst0.0に向いていること。
user01@FW-01> show route
inet.0: 16 destinations, 16 routes (16 active, 0 holddown, 0 hidden)
+ = Active Route, - = Last Active, * = Both
0.0.0.0/0 *[Static/5] 01:00:49
> to 10.153.92.190 via ge-0/0/2.0
(中略)
10.1.1.0/30 *[Direct/0] 03:00:35
> via st0.0
10.1.1.1/32 *[Local/0] 03:25:05
Local via st0.0
10.153.92.176/28 *[Direct/0] 01:00:49
> via ge-0/0/2.0
10.153.92.182/32 *[Local/0] 04:25:45
Local via ge-0/0/2.0
(中略)
192.168.11.0/28 *[Static/5] 03:00:35
> via st0.0
192.168.33.128/28 *[Direct/0] 01:00:49
> via ge-0/0/0.0
192.168.33.139/32 *[Local/0] 01:00:44
Local via ge-0/0/0.0
192.168.33.140/32 *[Local/0] 08:20:30
Local via ge-0/0/0.0
192.168.33.144/28 *[Direct/0] 01:00:49
> via ge-0/0/1.0
192.168.33.156/32 *[Local/0] 04:25:46
Local via ge-0/0/1.0
FW-02の拠点A(192.168.11.0/28)に対するルートがst0.1に向いていること。
user01@FW-02> show route
inet.0: 15 destinations, 15 routes (15 active, 0 holddown, 0 hidden)
+ = Active Route, - = Last Active, * = Both
0.0.0.0/0 *[Static/5] 04:10:58
> to 10.153.92.238 via ge-0/0/2.0
(中略)
10.2.1.0/30 *[Direct/0] 03:00:53
> via st0.1
10.2.1.1/32 *[Local/0] 03:23:34
Local via st0.1
10.153.92.224/28 *[Direct/0] 04:26:29
> via ge-0/0/2.0
10.153.92.227/32 *[Local/0] 04:26:29
Local via ge-0/0/2.0
(中略)
192.168.11.0/28 *[Static/5] 02:59:26
> via st0.1
192.168.33.128/28 *[Direct/0] 1d 01:08:53
> via ge-0/0/0.0
192.168.33.141/32 *[Local/0] 1d 01:08:53
Local via ge-0/0/0.0
192.168.33.144/28 *[Direct/0] 04:26:29
> via ge-0/0/1.0
192.168.33.157/32 *[Local/0] 04:26:29
Local via ge-0/0/1.0
user01@FW-03> show route
inet.0: 15 destinations, 16 routes (15 active, 0 holddown, 0 hidden)
+ = Active Route, - = Last Active, * = Both
0.0.0.0/0 *[Static/5] 04:13:46
> to 10.153.112.230 via ge-0/0/1.0
(中略)
10.1.1.0/30 *[Direct/0] 01:02:51
> via st0.0
10.1.1.2/32 *[Local/0] 03:56:01
Local via st0.0
10.2.1.0/30 *[Direct/0] 03:03:08
> via st0.1
10.2.1.2/32 *[Local/0] 03:56:01
Local via st0.1
10.153.112.224/29 *[Direct/0] 04:19:25
> via ge-0/0/1.0
10.153.112.227/32 *[Local/0] 04:19:25
Local via ge-0/0/1.0
(中略)
192.168.11.0/28 *[Direct/0] 1d 01:46:53
> via ge-0/0/0.0
192.168.11.12/32 *[Local/0] 1d 01:46:53
Local via ge-0/0/0.0
192.168.33.128/28 *[Static/5] 01:02:51
> via st0.0
[Static/7] 03:00:11
> via st0.1
Client端末の接続確認
pingコマンド、FTPコマンドが成功することを確認します。
pingコマンドを用いて通信確認[OK]
[user01@client ~]$ ping 192.168.33.131 -c 5
PING 192.168.33.131 (192.168.33.131) 56(84) bytes of data.
64 bytes from 192.168.33.131: icmp_seq=1 ttl=62 time=5.71 ms
64 bytes from 192.168.33.131: icmp_seq=2 ttl=62 time=1.60 ms
64 bytes from 192.168.33.131: icmp_seq=3 ttl=62 time=1.53 ms
64 bytes from 192.168.33.131: icmp_seq=4 ttl=62 time=1.70 ms
64 bytes from 192.168.33.131: icmp_seq=5 ttl=62 time=1.68 ms
--- 192.168.33.131 ping statistics ---
5 packets transmitted, 5 received, 0% packet loss, time 4007ms
rtt min/avg/max/mdev = 1.533/2.447/5.713/1.634 ms
[user01@client ~]$
FTPコマンドを用いて通信確認[OK]
[user01@client ~]$ ftp 192.168.33.131
Connected to 192.168.33.131 (192.168.33.131).
220 (vsFTPd 3.0.2)
Name (192.168.33.131:user01): user01
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp>
ftp> ls
227 Entering Passive Mode (192,168,33,131,85,247).
150 Here comes the directory listing.
-rw-r--r-- 1 1000 1000 1000000 Apr 17 11:52 TEST_FILE_1MB
226 Directory send OK.
ftp>
ftp> bi
200 Switching to Binary mode.
ftp>
ftp> get TEST_FILE_1MB
local: TEST_FILE_1MB remote: TEST_FILE_1MB
227 Entering Passive Mode (192,168,33,131,34,104).
150 Opening BINARY mode data connection for TEST_FILE_1MB (1000000 bytes).
226 Transfer complete.
1000000 bytes received in 0.047 secs (21268.00 Kbytes/sec)
ftp>
ftp> quit
221 Goodbye.
以上で正常時の確認を終了します。
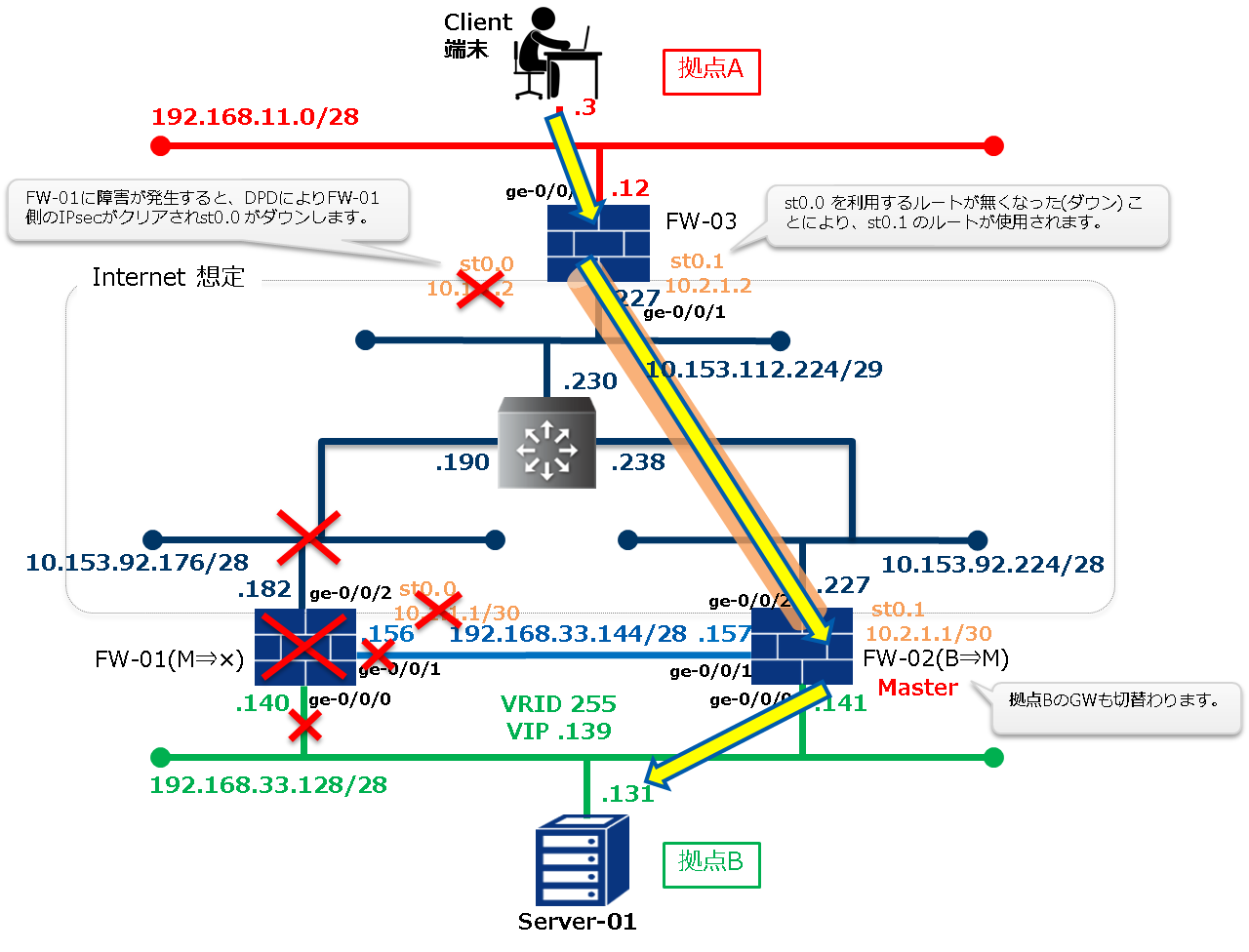
1.3.4. 障害発生時の通信の流れ¶
注釈
FW-03がDPDで異常を検知してから、ルートの切り替えが完了するまでには1分程度の時間がかかります。
注釈
インターフェイス無効化の設定コマンド
# set interfaces ge-0/0/0.0 disable# set interfaces ge-0/0/1.0 disable# set interfaces ge-0/0/2.0 disableインターフェイス有効化の設定コマンド
# delete interfaces ge-0/0/0.0 disable# delete interfaces ge-0/0/1.0 disable# delete interfaces ge-0/0/2.0 disable
障害発生時の状態確認
障害発生時のFWの状態は以下のように確認できます。
注釈
FW-01はインスタンス障害が発生しているためステータスの確認は省略しています。
VRRPの状態
FW-02がMasterであること。
user01@FW-02> show vrrp
Interface State Group VR state VR Mode Timer Type Address
ge-0/0/0.0 up 255 master Active A 0.091 lcl 192.168.33.141
vip 192.168.33.139
VPNの状態
FW-02とFW-03がVPNを確立できていること。
user01@FW-02> show security ike security-associations
Index State Initiator cookie Responder cookie Mode Remote Address
5424792 UP 456a8445e25a6152 ea6a957cded9d41e IKEv2 10.153.112.227
user01@FW-02>
user01@FW-02> show security ipsec security-associations
Total active tunnels: 1
ID Algorithm SPI Life:sec/kb Mon lsys Port Gateway
<131073 ESP:aes-gcm-256/None 9343a203 3565/ unlim - root 500 10.153.112.227
>131073 ESP:aes-gcm-256/None b7641ea6 3565/ unlim - root 500 10.153.112.227
FW-03とFW-02がVPNを確立できていること。
user01@FW-03> show security ike security-associations
Index State Initiator cookie Responder cookie Mode Remote Address
6898209 UP 456a8445e25a6152 ea6a957cded9d41e IKEv2 10.153.92.227
6898223 DOWN aebadb1ffd1f6145 0000000000000000 IKEv2 10.153.92.182
user01@FW-03>
user01@FW-03> show security ipsec security-associations
Total active tunnels: 1
ID Algorithm SPI Life:sec/kb Mon lsys Port Gateway
<131074 ESP:aes-gcm-256/None b7641ea6 3520/ unlim - root 500 10.153.92.227
>131074 ESP:aes-gcm-256/None 9343a203 3520/ unlim - root 500 10.153.92.227
インターフェイスの状態
FW-02のst0.1がUPしていること。
user01@FW-02> show interfaces terse | no-more
Interface Admin Link Proto Local Remote
ge-0/0/0 up up
ge-0/0/0.0 up up inet 192.168.33.139/28
192.168.33.141/28
gr-0/0/0 up up
ip-0/0/0 up up
lsq-0/0/0 up up
lt-0/0/0 up up
mt-0/0/0 up up
sp-0/0/0 up up
sp-0/0/0.0 up up inet
inet6
sp-0/0/0.16383 up up inet
ge-0/0/1 up up
ge-0/0/1.0 up up inet 192.168.33.157/28
ge-0/0/2 up up
ge-0/0/2.0 up up inet 10.153.92.227/28
(中略)
st0 up up
st0.1 up up inet 10.2.1.1/30
tap up up
vlan up down
vtep up up
FW-03のst0.0がDOWNしており、st0.1がUPしていること。
user01@FW-03> show interfaces terse | no-more
Interface Admin Link Proto Local Remote
ge-0/0/0 up up
ge-0/0/0.0 up up inet 192.168.11.12/28
gr-0/0/0 up up
ip-0/0/0 up up
lsq-0/0/0 up up
lt-0/0/0 up up
mt-0/0/0 up up
sp-0/0/0 up up
sp-0/0/0.0 up up inet
inet6
sp-0/0/0.16383 up up inet
ge-0/0/1 up up
ge-0/0/1.0 up up inet 10.153.112.227/29
(中略)
st0 up up
st0.0 up down inet 10.1.1.2/30
st0.1 up up inet 10.2.1.2/30
tap up up
vlan up down
vtep up up
ルーティングの状態
FW-02の拠点A(192.168.11.0/28)に対するルートがst0.1に向いていること。
user01@FW-02> show route
inet.0: 16 destinations, 16 routes (16 active, 0 holddown, 0 hidden)
+ = Active Route, - = Last Active, * = Both
0.0.0.0/0 *[Static/5] 08:44:39
> to 10.153.92.238 via ge-0/0/2.0
(中略)
10.2.1.0/30 *[Direct/0] 04:11:32
> via st0.1
10.2.1.1/32 *[Local/0] 07:57:15
Local via st0.1
10.153.92.224/28 *[Direct/0] 09:00:10
> via ge-0/0/2.0
10.153.92.227/32 *[Local/0] 09:00:10
Local via ge-0/0/2.0
(中略)
192.168.11.0/28 *[Static/5] 04:11:32
> via st0.1
192.168.33.128/28 *[Direct/0] 1d 05:42:34
> via ge-0/0/0.0
192.168.33.139/32 *[Local/0] 00:03:23
Local via ge-0/0/0.0
192.168.33.141/32 *[Local/0] 1d 05:42:34
Local via ge-0/0/0.0
192.168.33.144/28 *[Direct/0] 09:00:10
> via ge-0/0/1.0
192.168.33.157/32 *[Local/0] 09:00:10
Local via ge-0/0/1.0
FW-03の拠点B(192.168.33.128/28)に対するルートがst0.1に向いていること。
user01@FW-03> show route
inet.0: 14 destinations, 14 routes (14 active, 0 holddown, 0 hidden)
+ = Active Route, - = Last Active, * = Both
0.0.0.0/0 *[Static/5] 08:45:16
> to 10.153.112.230 via ge-0/0/1.0
(中略)
10.1.1.2/32 *[Local/0] 08:27:31
Reject
10.2.1.0/30 *[Direct/0] 04:11:37
> via st0.1
10.2.1.2/32 *[Local/0] 08:27:31
Local via st0.1
10.153.112.224/29 *[Direct/0] 08:50:55
> via ge-0/0/1.0
10.153.112.227/32 *[Local/0] 08:50:55
Local via ge-0/0/1.0
(中略)
192.168.11.0/28 *[Direct/0] 1d 06:18:23
> via ge-0/0/0.0
192.168.11.12/32 *[Local/0] 1d 06:18:23
Local via ge-0/0/0.0
192.168.33.128/28 *[Static/7] 04:11:37
> via st0.1
Client端末の接続確認
pingコマンド、FTPコマンドが成功することを確認します。
pingコマンドを用いて通信確認[OK]
[user01@client ~]$ ping 192.168.33.131 -c 5
PING 192.168.33.131 (192.168.33.131) 56(84) bytes of data.
64 bytes from 192.168.33.131: icmp_seq=1 ttl=62 time=7.63 ms
64 bytes from 192.168.33.131: icmp_seq=2 ttl=62 time=1.41 ms
64 bytes from 192.168.33.131: icmp_seq=3 ttl=62 time=1.66 ms
64 bytes from 192.168.33.131: icmp_seq=4 ttl=62 time=1.47 ms
64 bytes from 192.168.33.131: icmp_seq=5 ttl=62 time=1.64 ms
--- 192.168.33.131 ping statistics ---
5 packets transmitted, 5 received, 0% packet loss, time 4006ms
rtt min/avg/max/mdev = 1.412/2.766/7.633/2.435 ms
FTPコマンドを用いて通信確認[OK]
[user01@client ~]$ ftp 192.168.33.131
Connected to 192.168.33.131 (192.168.33.131).
220 (vsFTPd 3.0.2)
Name (192.168.33.131:user01): user01
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> ls
227 Entering Passive Mode (192,168,33,131,178,134).
150 Here comes the directory listing.
-rw-r--r-- 1 1000 1000 1000000 Apr 17 11:52 TEST_FILE_1MB
226 Directory send OK.
ftp>
ftp> bi
200 Switching to Binary mode.
ftp>
ftp> get TEST_FILE_1MB
local: TEST_FILE_1MB remote: TEST_FILE_1MB
227 Entering Passive Mode (192,168,33,131,163,18).
150 Opening BINARY mode data connection for TEST_FILE_1MB (1000000 bytes).
226 Transfer complete.
1000000 bytes received in 0.0468 secs (21372.09 Kbytes/sec)
ftp>
ftp> quit
221 Goodbye.
以上で障害発生時の確認を終了します。