IoT SAFE [English]¶
What is IoT SAFE?¶
IoT SAFE (IoT SIM Applet For Secure End-2-End Communication) is a standard defined by the GSMA to use SIM cards as the Root of Trust for secure communication between IoT devices and the cloud.
By incorporating a SIM applet with authentication and encryption functions, it provides secure device authentication and end-to-end data encryption, and it is considered a key technology for ensuring device security in IoT devices using cellular networks.
This applet has been developed in compliance with IoT SAFE standard specifications.
Overview of IoT SAFE¶
IoT SAFE operates in the following sequence:
Preliminary Tasks
Install the IoT SAFE applet on the SIM card.
From either the “IoT SAFE” menu or the OpenAPI, register either the “SIM-specific identification information” or the “identification template.”
Certificate Generation Process
When launched, the IoT SAFE applet generates a key pair and then contacts the Applet Console to verify commands.
The Applet Console issues a command (ReadPublicKey command) to instruct the reading of the public key.
The IoT SAFE applet sends the public key of the generated key pair to the Applet Console.
The Applet Console instructs the generation and submission of a CSR (GenerateCSR command).
The IoT SAFE applet generates the CSR and sends it to the Applet Console.
The Applet Console signs a client certificate based on the submitted CSR.
The Applet Console distributes the client certificate using the DeliveryClientCert command.
Usage of the Client Certificate
Establish mTLS and VPN communications.
As a result of these operations, the IoT SAFE applet stores the key pair (private and public keys), CSR, and client certificate, enabling secure communications.
Verification of IoT SAFE¶
This section demonstrates how to verify " the mTLS communication " and "the VPN communication" between the IoT SAFE applet and Applet Console.
Verification Environment¶
This verification requires the following software and hardware:
IoT Device
- Raspberry Pi
Debian GNU/Linux 12 (bookworm)
OpenSSL 3.0.11
- device
For supported models, please refer to here.
IoT Server
- Any web server, etc.
Must be configured to require client certificate verification.
VPN Server
- A VPN server with OpenVPN
Must be configured to require client certificate verification.
Applet Console
Used for applet installation and verification of public keys and CSR.
Prerequisites¶
- Install the packages (libifd-atcmd and pkcs11-iotsafe) necessary to run IoT SAFE on Linux.
By installing the IoT SAFE Client, you can install all required packages at once.
For the IoT SAFE Client installation method, please refer to here.
For other commands available for the IoT SAFE Client, please refer to here.
Installation of IoT SAFE Applet¶
- Install the IoT SAFE applet on the SIM card.
Please refer to Applet Consoleの操作方法
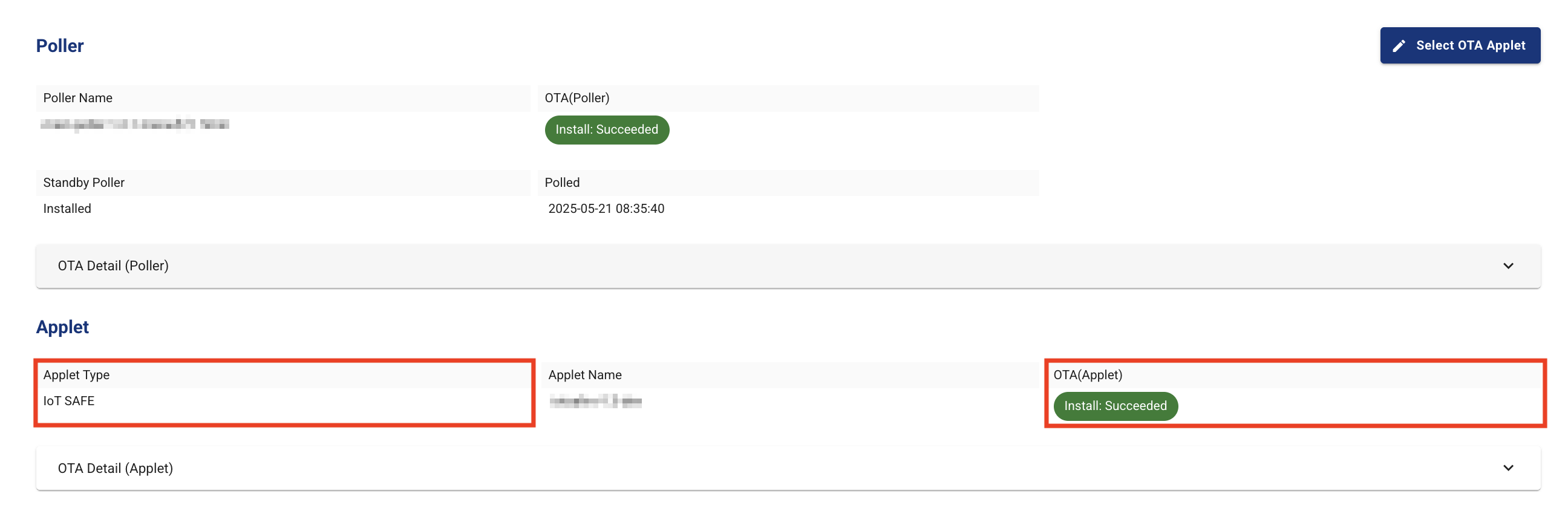
- Confirm that the IoT SAFE applet has been successfully installed on the SIM card.
From the SIM menu of the Applet Console, open the SIM detail screen of the corresponding SIM card.
Confirm that the OTA status is "Install:Succeeded".
Identification Information Registration in Applet Console¶
- Register either "SIM-specific identification information" or an "identification template".
In this example, we will demonstrate how to register the "identification template".
注釈
If the identification template has already been registered, this step is not necessary. Please proceed to "Generate CSR and Sign the Client Certificate".
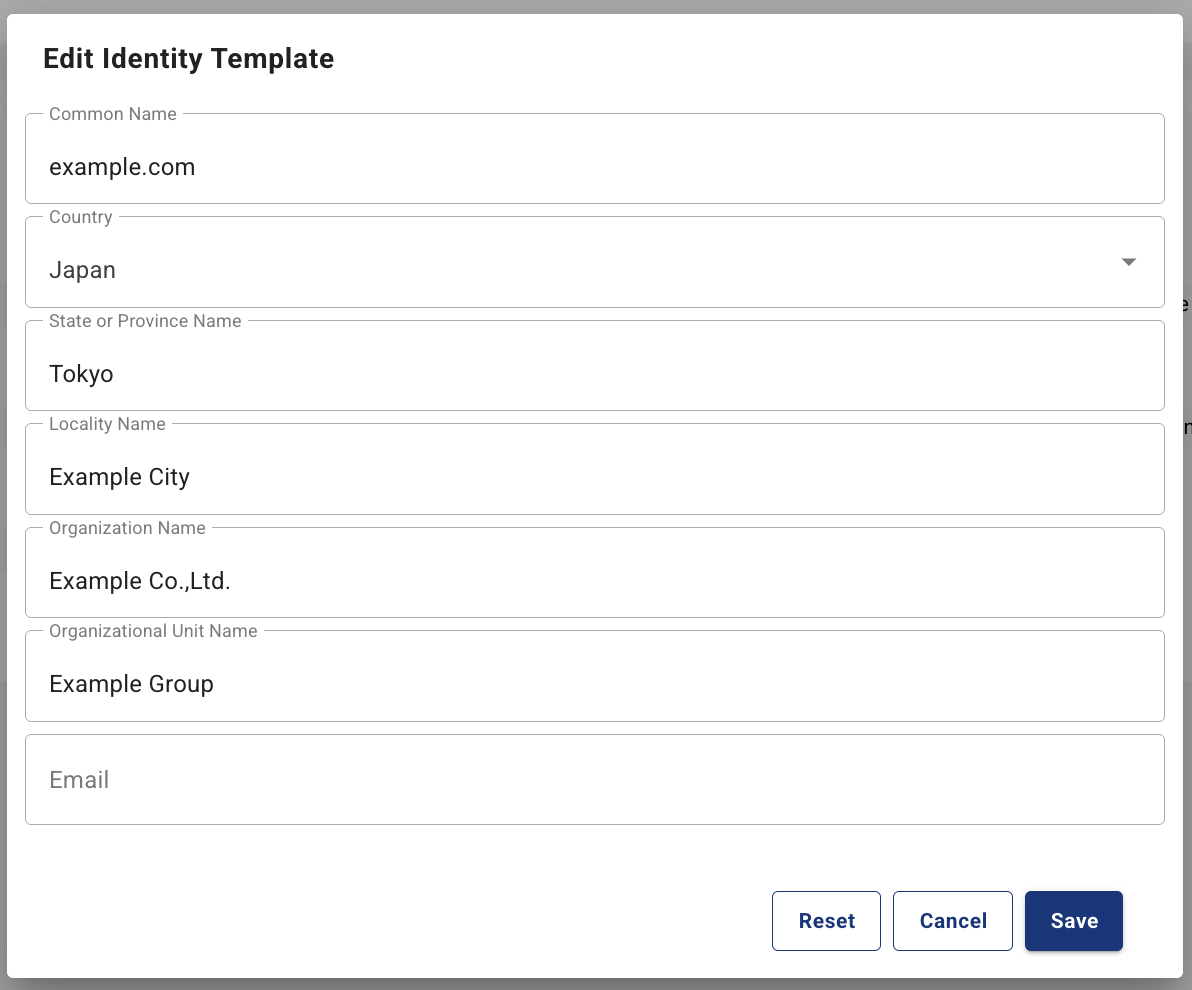
- From the Settings menu > IoT SAFE tab > Identification Template tab, click the "Edit" button to edit the identification template.
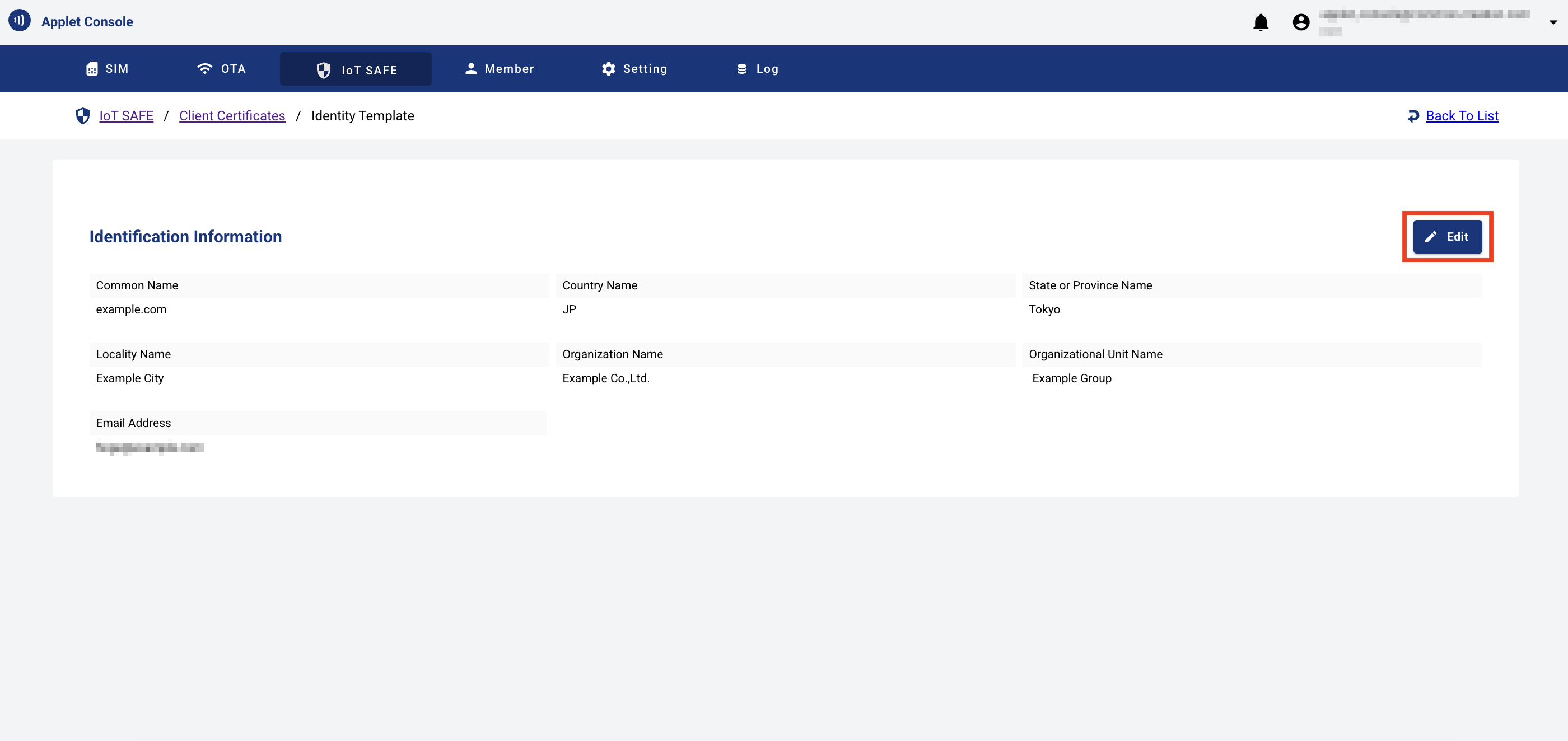
Confirm that the identification template has been registered.
CSR Generation and Client Certificate Signing¶
Power on the IoT device and launch the IoT SAFE applet.
- From IoT SAFE menu > {ICCID of the SIM where the IoT SAFE applet is installed} > Client Certificate list, click the "ID" to display the client certificate details.
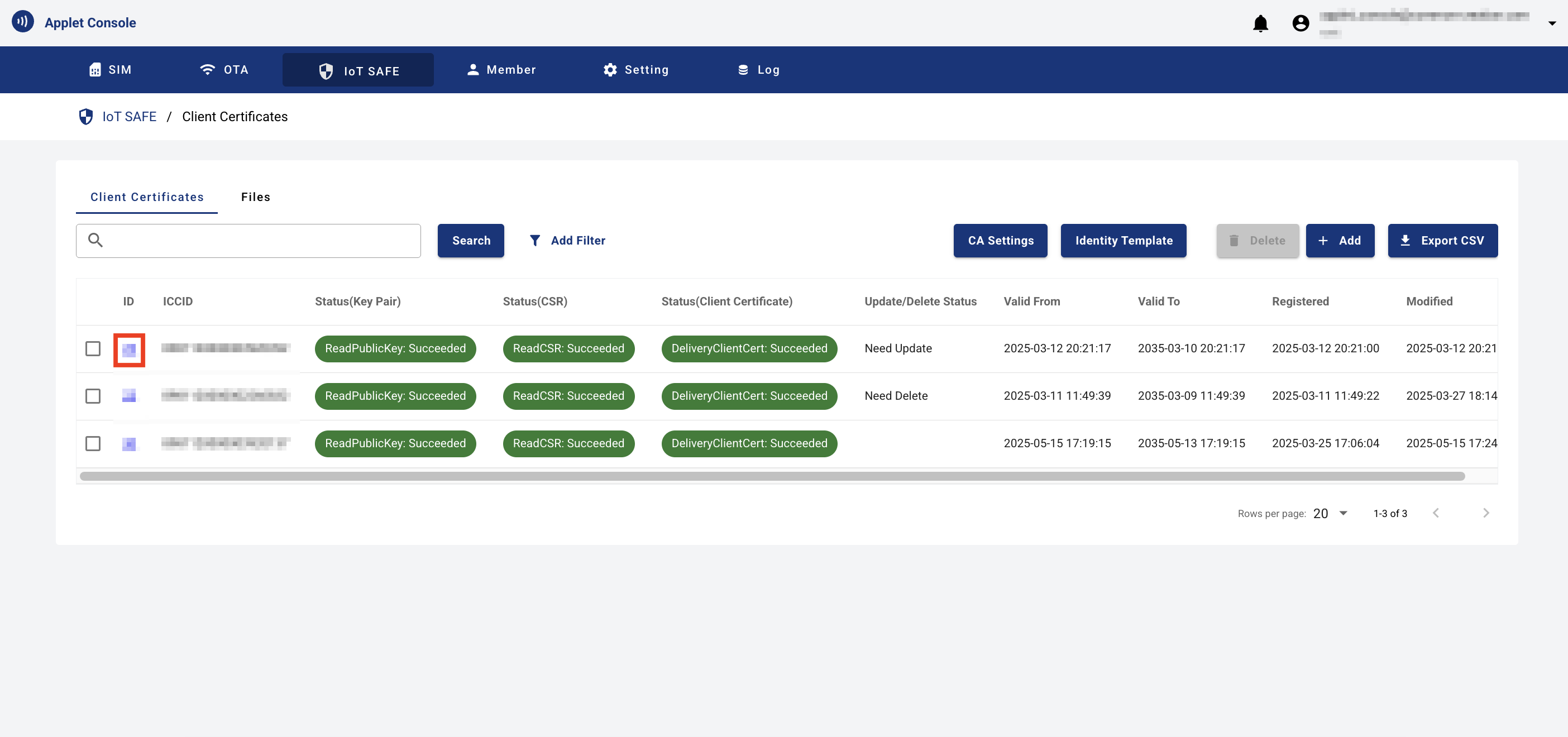
- Confirm that the results of the ReadPublicKey command, ReadCSR command, and DeliveryClientCert command have all succeeded.
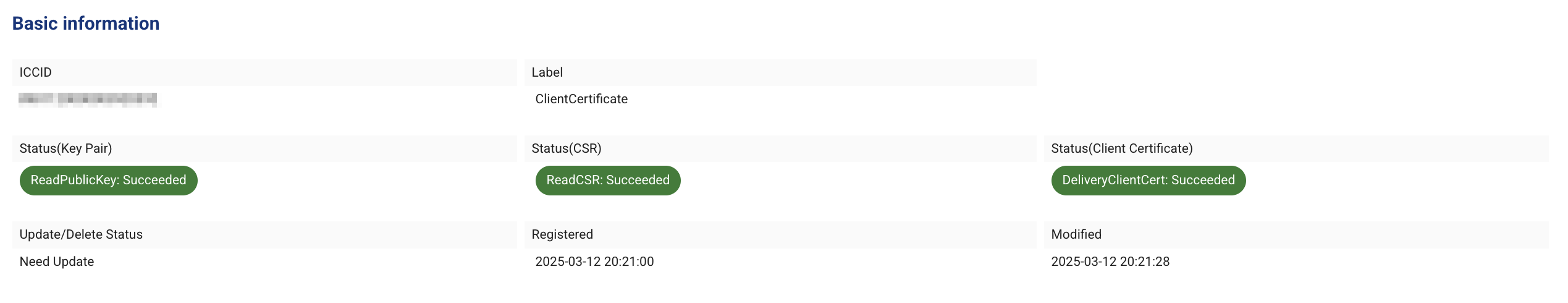
- Public keys, CSRs, and client certificates can also be checked from “PEM format data” on the same screen.

File Distribution¶
Configuration files and other data can be distributed to the IoT SAFE applet.
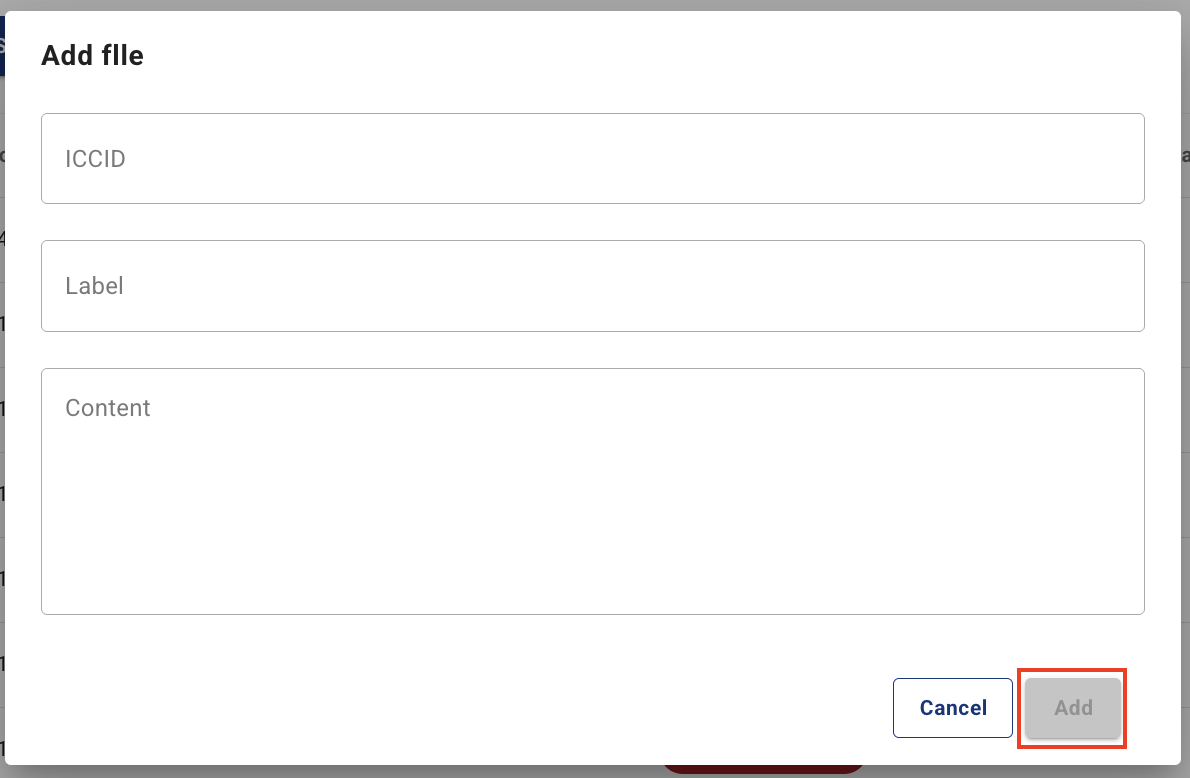
- From IoT SAFE menu > {ICCID of the SIM where the IoT SAFE applet is installed} > File list, click the “Add” button.
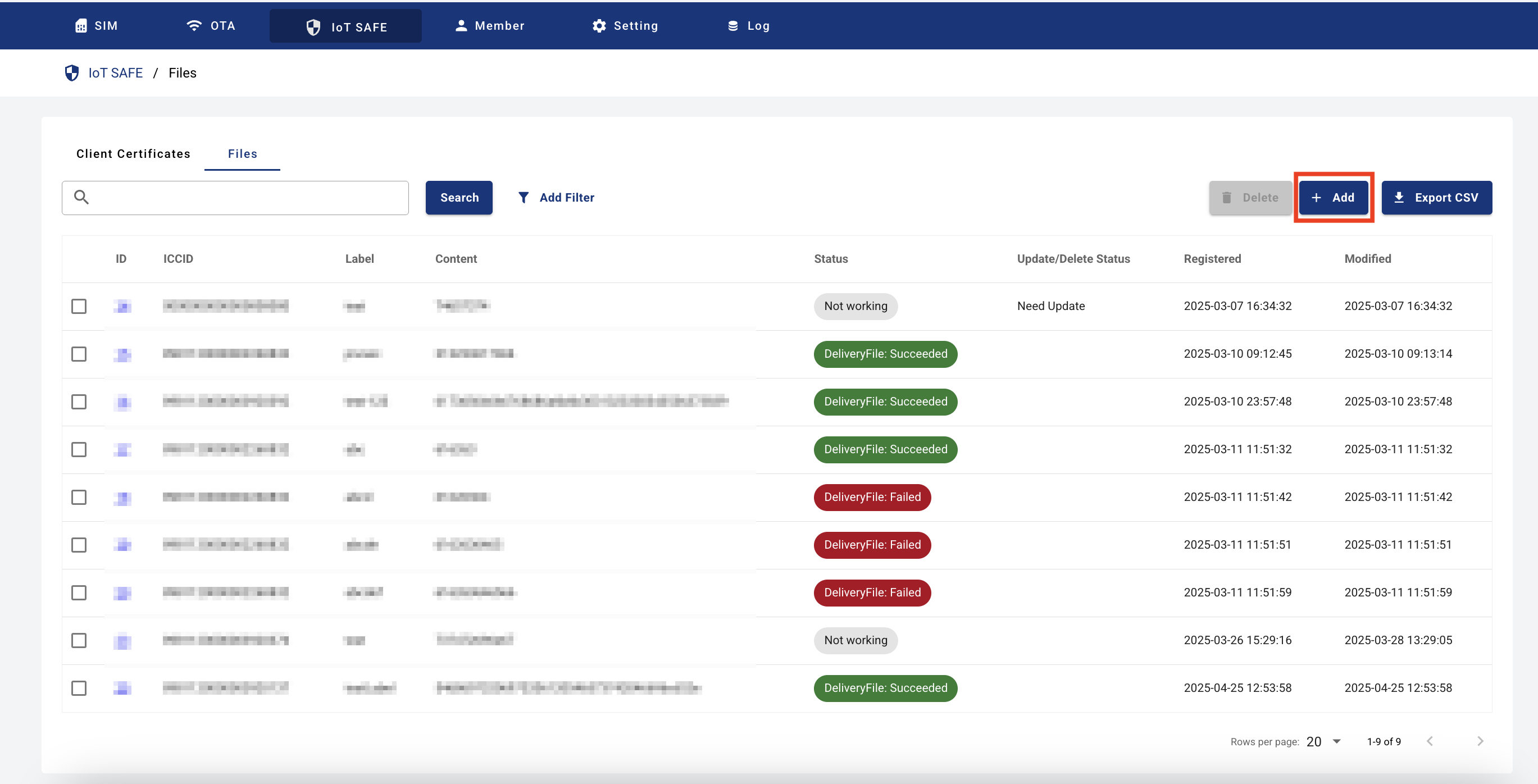
Turn on the IoT device and start the IoT SAFE applet.
- Clicking on the “ID” displayed in the file list will display detailed information about the file.
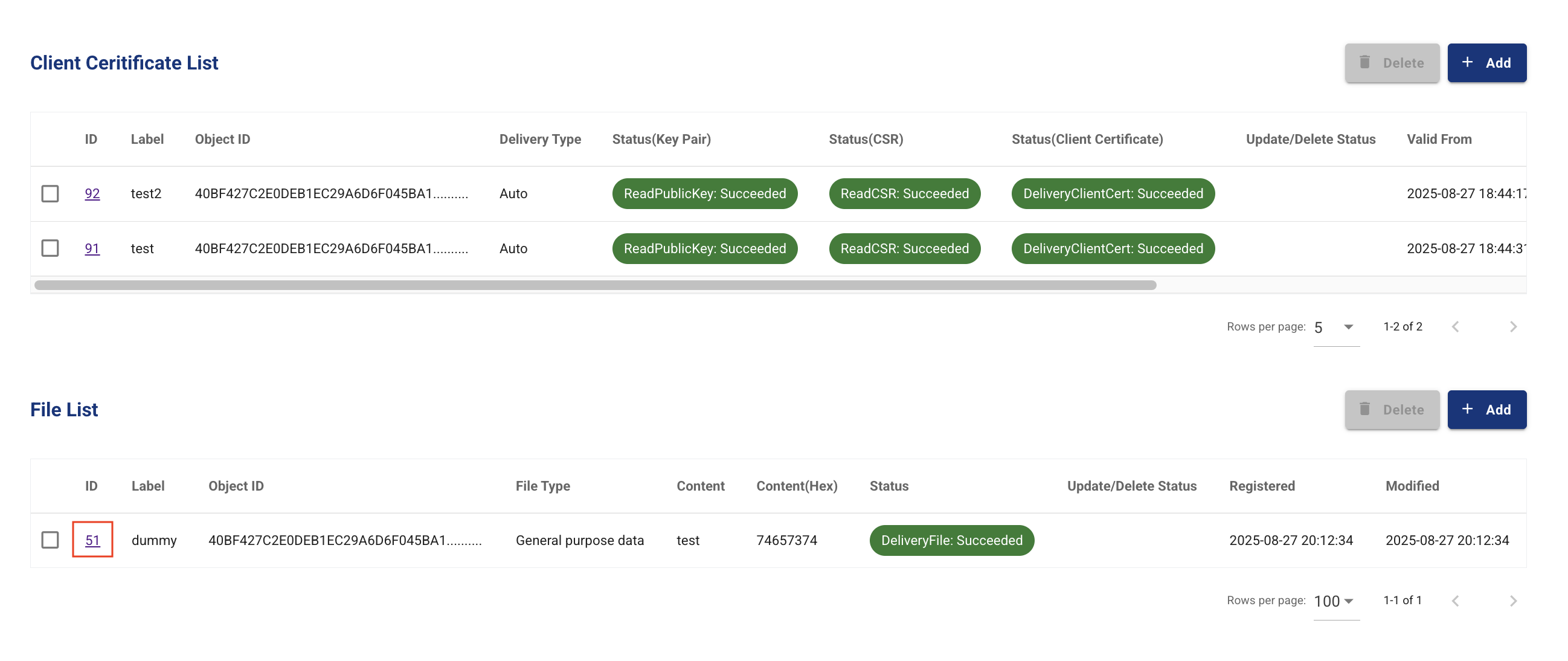
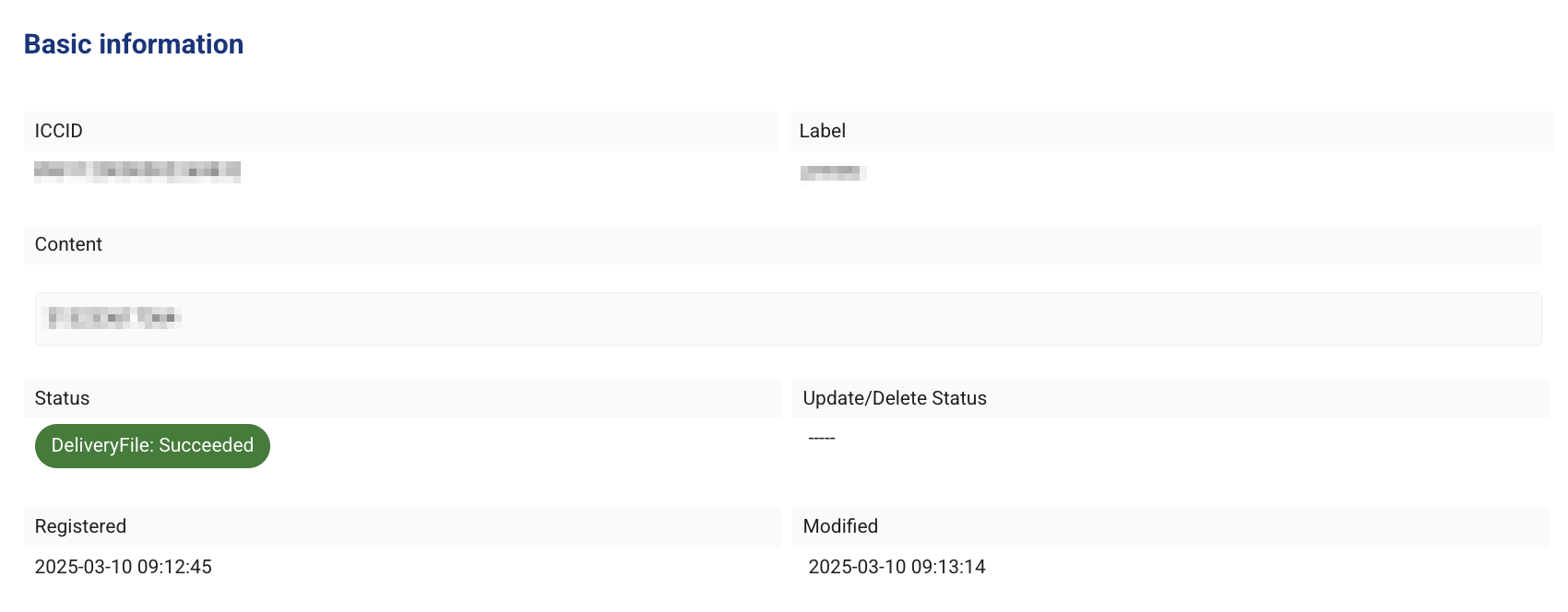
- Confirm that the result of the DeliveryFile command is Succeeded.
Obtaining an object ID¶
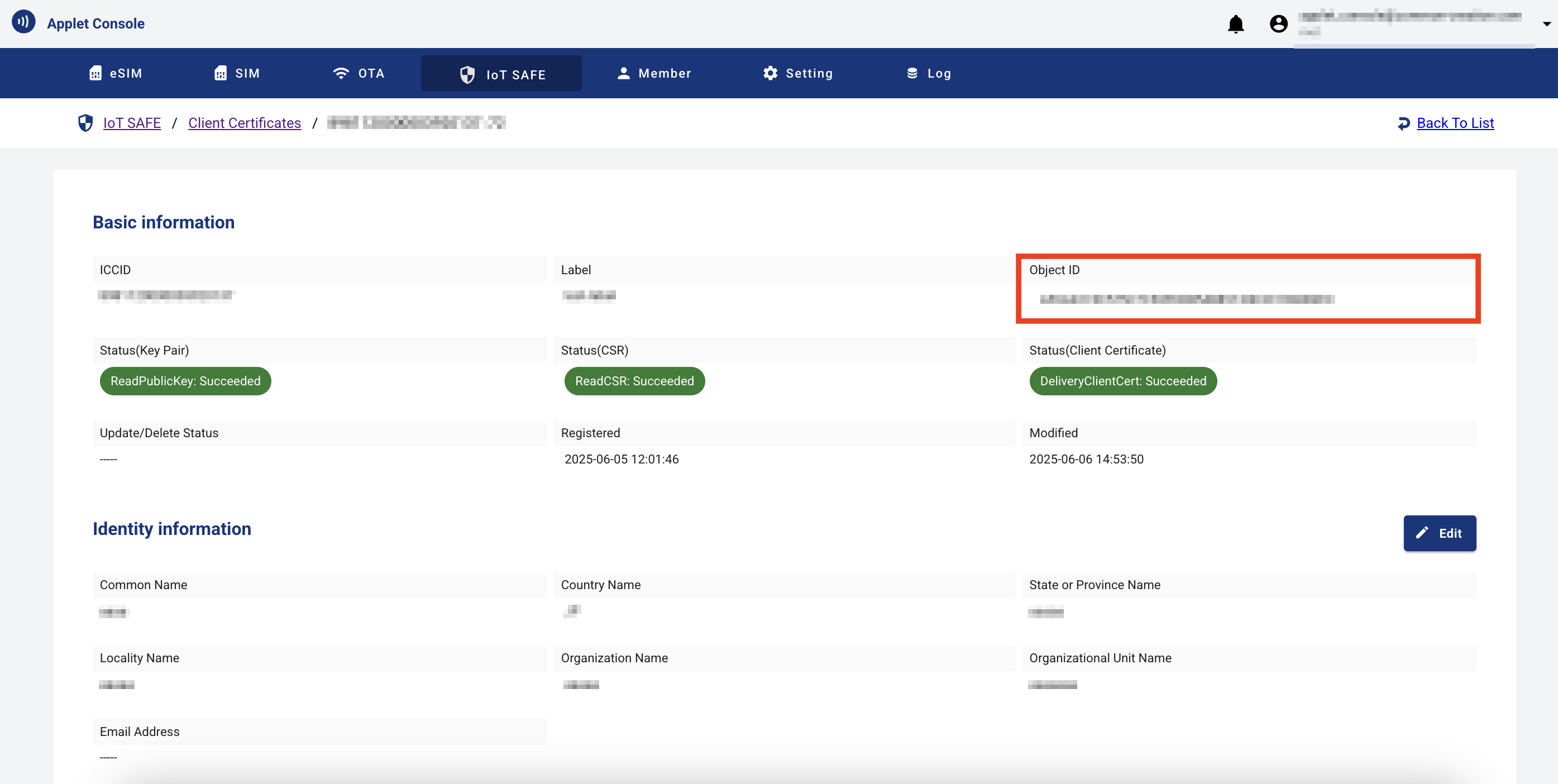
Obtain the object ID of the client certificate distributed to the IoT SAFE applet.
- From IoT SAFE menu > {ICCID of the SIM where the IoT SAFE applet is installed} > Client Certificate list, click the "ID" to display the client certificate details.

- Check the “Object ID” displayed in the “Basic Information” section of the client certificate details screen.
Establishing mTLS Communication¶
- Connect to the IoT server using mTLS communication.
openssl s_client \ -connect IP address of IoT server:port number of IoT server \ -cert "pkcs11:token=IoTSAFE;type=cert;id={object ID}" \ -key "pkcs11:token=IoTSAFE;type=private;id={object ID}"
Establishing VPN Communication when using IoT SAFE Client¶
- Connect to the VPN server using OpenVPN.
iotsafe-client vpn start
- Check the connection status.
iotsafe-client vpn status